ANALYSIS of the modern world experience of military operations shows that their successful implementation requires timely comprehensive information support for combat operations, covert command and control, and the use of high-precision weapons.
Combat operations are controlled from the command posts of the highest, operational-strategic, and tactical levels. In any case, control points are equipped with local information networks, computer equipment, which include an operating system (OS), a database management system (DBMS), security and access systems.
Weapon systems, including missiles, aircraft, helicopters, submarines and surface ships, air and missile defense systems, high-precision weapons, and command and control centers are equipped with similar means.
TO THE HISTORY OF THE QUESTION
Since the 1960s began to develop rapidly electronic computers, it has become one of the priority components of the country's defense potential. At the same time, the following priorities were set as priorities:
Ensuring the automation of command and control of troops and weapons in order to increase, on this basis, the effectiveness of combat operations and the use of weapons;
- training of personnel of the Armed Forces of the Russian Federation in free and professional possession and use information technologies both in daily activities and in command and control of troops in the course of hostilities and possession of weapons.
During these years, unprecedented measures were taken: large research and design centers were built and equipped (the "city of electronics" Zelenograd, a number of organizations and enterprises in Moscow, Penza, Kyiv, Kazan, Minsk and other cities); international cooperation was organized, special ministries and departments were created; a special methodology for the parallel development and implementation of information technologies has been formed in almost all the main areas of activity of the Armed Forces of the Russian Federation.
And it must be said frankly that these measures have made it possible to dramatically increase the level of automation of the processes of command and control of troops and weapons in the army and navy, as well as the level of computer literacy of the personnel of our Armed Forces.
The industry began to develop various types of computers and operating systems, or to use foreign designs available for them.
At the same time, we were faced with a process of increasing negative trends, which to a large extent began to slow down the further effective development and use of modern information technologies.
The Armed Forces have accumulated unjustifiably big variety software, software, information technology is mainly foreign-made. Suffice it to say that about 60 types of operating systems, about 50 types of database management systems, more than 100 information exchange protocols are currently used. In addition, many of these software tools do not have the necessary protection tools.
This situation has developed as a result of the lack of a single software and hardware platform, hundreds of duplicating developments of software and hardware complexes and automated systems for various purposes.
This, in turn, led to a multiple increase in financial costs and time for duplicating developments, as well as to a technological lag and significant dependence on imported technology. The control systems created on their basis tore apart the information space of the Armed Forces of the Russian Federation into a large number of incompatible fragments, reduced their security, which ultimately led to potential vulnerabilities in information warfare.
At present, the situation has become even more aggravated due to the appearance in a number of countries of the so-called information weapon. It can be a tool for:
Targeted impact on the control systems of other countries and their law enforcement agencies (distortion, formation and imposition of false information, its destruction);
- committing terrorist acts against state administration systems, law enforcement agencies, life support industries and the economy (communications, transport, fuel complex, energy complex, finance, etc.);
- destruction of automated systems.
Elements of information weapons can also be included in imported software.
Therefore, automated military systems built on foreign software cannot provide the necessary degree of information security and technological independence of the country and the Armed Forces.
I would like to draw attention to special kind threats in the "information war" - the desire of developed foreign countries to contain the Russian information technology industry while counteracting Russia's access to the latest information technologies. In fact, the world's leading firms do not hide their intentions to seize the information technology of the Russian Armed Forces. There was a threat of constant technological dependence on foreign suppliers of information technology.
Under these conditions, only domestically protected basic information technologies can ensure the unity of the weapons system, its security and technological independence. Russian teams must create and support software and hardware products at all stages of their life cycle.
EXIT FROM THE CURRENT SITUATION
Realizing the need to create a single secure domestic software and hardware platform, the Russian Ministry of Defense in 1994 decided to develop domestic basic information technologies (including operating systems, database management systems, development tools and software and hardware complexes).
The decision was also made on the basis of an analysis of the current world experience in conducting military operations, which showed that the most important factors Their success is determined by the timely comprehensive information support of combat operations, covert command and control, and the use of high-precision weapons. This is very clearly demonstrated by the events of local conflicts. recent years(Yugoslavia, Afghanistan, Iraq).
By order of the Ministry of Defense of the Russian Federation, domestic means of basic information protected computer technologies were created, carried out state tests and accepted for supply to the Armed Forces: the MCVS operating system, the Linter-VS database management system and the Holst-S software and hardware complex.
An analysis of the characteristics of these tools and foreign analogues shows the advantages of domestic developments, primarily in terms of reliability, protection against unauthorized access, warranty service, maintenance and support in a special period.
These tools can be used to process information that contains state secrets.
The software is commercially supplied both independently and as part of standard protected software and hardware systems.
The flexible structure of the "Holst-C" complex allows it to be delivered in the required configuration and with the necessary computing power in accordance with the needs of a particular automation object.
Recently, the Ministry of Defense of the Russian Federation, taking into account economic efficiency a number of decisions were made to pursue a unified scientific and technical policy in the Armed Forces in the field of military basic information technologies, including new organization orders and work on the creation of automated military systems based on domestic technologies.
These decisions determined the procedure for coordinating the development of new systems based on basic information technologies both within the Ministry of Defense and with the main developers of automated military systems.
The Chief of Armaments of the Armed Forces of the Russian Federation has been entrusted with a fundamentally new task of coordinating tactical and technical specifications for the creation of automated means, command and control systems for troops and weapons by type of support (mathematical, software, technical, informational, linguistic), integrated information protection and software and hardware complexes.
It has been established that automated means, command and control systems for troops and weapons will be accepted into service (in operation, for supply) only if they are created on the basis of domestic basic information protected computer technologies. In accordance with the decisions taken, these principles are being actively implemented into the practice of developing and modernizing information technology systems.
Of course, the introduction of this technology is not without conflict. We encounter often quite stubborn opposition from some developers and organizations. And this is not something out of the ordinary. This is a normal process of introducing a new one. Moreover, we perfectly understand the position of the resisters. After all, we are talking about the need to refine, and sometimes remake the worked out and implemented software products. But life inexorably dictates the need to switch to modern secure technologies. All software developers need to realize this and look for ways to optimally solve this problem.
It should also be noted that the leaders of a number of leading industrial organizations prepared teams in a timely manner and have already reached the modern technological level. Unfortunately, individual organizations - developers of automated control systems have not yet been able to do this.
PERSPECTIVE
The Ministry of Defense pays special attention to the issues of creating informationally interconnected automated control systems for all levels based on unified and standardized software, technical and information-linguistic means of basic technologies.
The priority task is the further development of basic military information technologies in order to create the foundations for building a single information space, including systems that make it possible to build end-to-end control paths from combined-arms command posts to direct means of fire impact.
These activities are expected to:
Create integrated automated military systems with "seamless" technology of joints within a single information space;
Reduce the range of work performed, duplicated in the development of automated control systems for all levels of command of types, branches of the armed forces, main and central departments and the costs of their creation;
To shorten the time for creating automated control systems by switching to the technology of using serial products and, accordingly, reduce financial costs.
A LITTLE ECONOMY
Serial deliveries of the basic secure information technology components common to all automated control systems will allow, when developing the system, to release funds in the amount of 25-30% of its total cost, directing them to the development of special software, and thereby focus the efforts of developers on the implementation of the full functional purpose of the system.
At the same time, the terms of creating systems are reduced by 2-3 years. Through the introduction of modern information technologies and computer technology in the modernization of weapons, it is possible to increase its efficiency from 10 to 30%. In addition, software products such as the operating system and database management system have good export potential. The volume of sales of these software tools by only three firms (IBM, Microsoft, Oracle) is about 80-100 billion dollars a year.
Since OS and DBMS with protection tools are not freely sold on the world market, we can conclude that there are good export prospects along with the supply of weapons and military equipment, and domestically developed software products.
Today, all power ministries and departments support the policy of the Ministry of Defense and are interested in creating secure information automated systems based on basic military technologies. This policy will be steadily implemented.
Otherwise it can not be. The price of the issue is too high - after all, up to 20% of the state defense order is annually allocated for the creation of automated systems for various purposes.
I would like to hope that the leading developers of automated control systems for troops and weapons are aware of this military-technical policy and the requirements of the Russian Ministry of Defense in such an important area.
SCIENCE AND MILITARY SECURITY No. 4/2008, pp. 11-17
ARMED FORCES MANAGEMENT
UDC 358.111.6
Major GeneralM.V. PUZIKOV ,
Chief of Missile Troops and Artillery of the Armed Forces -
Head of the Rocket and Artillery Department
of the General Staff of the Armed Forces, Candidate of Military Sciences
ColonelVC. SINYAVSKY ,
Head of the Department of the General Staff
Armed Forces, Doctor of Military Sciences
The experience of wars and armed conflicts of our time shows that one of the main conditions for achieving success on the battlefield is to get ahead of the enemy in reconnaissance and delivering missile strikes and artillery fire. One of the priority areas for achieving this is a comprehensive increase in the effectiveness of command and control of the armed forces. Increasing the efficiency of command and control processes is currently regarded as the highest priority in the development of missile forces and artillery (RV&A). Already today it is obvious that the future of M&A is directly related to the integrated automation of management processes at all levels. The article proposes the main approaches to determining the appearance automated system control (ACS) of the MFA as an integral part of the ACS of the Armed Forces.
Analysis combat use The MFA in modern armed conflicts has shown that at present the combat capabilities of the armed forces are realized only by 40 - 50%. This is due to the high dynamism and uncertainty of the current operational situation, the growth in the number of highly maneuverable targets and their increasing resistance, as well as the low level of development of intelligence, control and support subsystems.
An analysis of the contribution of each of the subsystems to the implementation of the combat capabilities of the MFA allowed us to draw two fundamental conclusions [1]:
1. The realizable share of the combat potential of the destruction subsystem is determined by the capabilities of the “weakest” of the subsystems.
2. No improvement of the "stronger" subsystems leads to an increase in the realizable share of the combat potential of the MFA group as a whole.
The most important practical consequence follows from these conclusions: a step-by-step increase in combat effectiveness requires the consistent identification of the weakest link. Calculations of the contribution of each subsystem to the effectiveness of the combat use of RV&A showed that with state of the art branches of the armed forces the weakest link is the control subsystem. Consequently, its improvement is a top-priority direction of increasing the combat effectiveness of the MFA.
AT modern conditions command and control of the armed forces can be effective only if it reacts almost instantly, in real time, to an incompletely defined and constantly changing operational situation. Achieving this level is possible only through the comprehensive automation of the processes of command and control of the MFA, both in peacetime and in wartime.
It is already becoming obvious today that without a clear definition of the goals of automation and a scientifically based distribution of control functions between headquarters at various levels, it is impossible to begin to determine the appearance of the M&A ACS. In the article, under the guise of ACS we will understand the structural and functional state of the contours of the system, quantitative and qualitative indicators, as well as the essence and content of control processes to be automated.
An analysis of the experience of operational and combat training of troops shows that the most complete implementation of the tasks facing the headquarters of the MFA is possible only under conditions of extensive automation of command and control processes within the framework of a single integrated automated control system of the Armed Forces.
Rice. 1. The main processes of command and control of missile forces and artillery to be automated

Rice. 2. A variant of the calculated control tasks solved by the headquarters of the missile forces and artillery at the stage of developing the concept of the operation
At the same time, the main goal of automating the control system should be considered to be the maximum possible increase in the efficiency of solving control problems and thereby ensuring a given level of efficiency and validity of control processes.
One of the most important issues on the way to automation is a clear definition of the list and content of processes and management tasks to be automated. An analysis of the functional activities of the headquarters showed that the management tasks solved in the headquarters of various levels of the hierarchy are basically similar in sequence and content. They are a series of interrelated sequential processes presented in Figure 1.
In the automated control system, all processes of command and control of troops and weapons should be implemented through information-computing processes (ICP) associated with the solution of information, operational-tactical and computational tasks at automated workstations (AWS) of automation equipment complexes (CSA).
At the same time, the solution of information problems should be aimed at filling the databases with information on the relevant applied areas (own troops, enemy troops, conditions for conducting combat operations, etc.). They implement mechanisms for selecting data from databases with elements of information processing according to specified conditions.
In turn, the solution of operational-tactical and computational problems should ensure the processing of accumulated information according to specified algorithms and criteria. The result of their decision should be aimed at the maximum possible validity of the decisions made. The variant of the calculation tasks solved by the MFA headquarters at the stage of developing the concept of the operation is shown in Figure 2.
In the aggregate, it is advisable to integrate all information and calculation tasks into complexes of control tasks, a variant of which is shown in Figure 3.
IVP in the M&A ACS should be built taking into account the following principles:
processing and transmission of information should be carried out in accordance with uniform algorithms for receiving information, solving problems of managing, registering, documenting and ensuring the security of information;
ensuring the stability and integrity of the IRP in the event of failure of individual elements of the system, as well as failures and failures of software and hardware;
the use of distributed local area networks (LAN) as the basis of the ICP;
unification of special mathematical and software within the framework of automated control systems;
determination of the nomenclature and powers of officials to applied functions and operational-tactical data, as well as the autonomy of the databases of the automated workplace of officials within the limits of their rights of access to information;
integration into the server database of the control point of the local databases of the workstation.

Rice. 3. A variant of the complexes of tasks for the control of missile forces and artillery

Rice. 4. A variant of the decision-making technology in the conditions of automation of the control system
At present, the method of constructing a TRS at control points using a LAN is the most promising. It allows you to significantly improve the characteristics of information transmission through the use of standard network protocols, as well as the distribution of information processing functions between network nodes (server, gateway and client). At the same time, the information processing technology is determined by its type and is a set of typical operations data processing in accordance with functional responsibilities officials, implemented on the workstation. It should be noted that the interaction of objects within the control center should be carried out on the basis of technologies for the interaction of open systems.
The implementation in practice of the principles of organization of the IVP will really simplify the decision support process in terms of automation and, as a result, increase the efficiency of the management process. A variant of the decision-making technology in the conditions of automation of the control system is shown in Figure 4.
Let's consider the contours of the ACS of the RV&A. In our opinion, it should be an integrated subsystem, fully integrated with the ACS of the Armed Forces, providing automated control of subordinate formations in any conditions of the operational situation. It should form a full-scale integrated system of automated command and control of troops, reconnaissance and weapons.
According to its structural and functional purpose, the MFA ACS should include subsystems of missile formations, large-caliber rocket artillery formations, MFA formations and combined arms formations. At the same time, the unification subsystem should be a set of automated subsystems of artillery units and artillery of combined arms combined into a single integrated system, coupled with automated control systems for reconnaissance, combat, rear and technical support.
It should cover all levels of control from strategic to tactical, and in the subsystem of destruction and reconnaissance to a specific means of reconnaissance and destruction. A variant of the structural-functional diagram of the M&A ACS is shown in Figure 5.
To realize its purpose, the MFA ACS must comply with the following principles of construction and operation:
Creation of an integrated M&A ACS based on unified information, linguistic, mathematical and software systems, uniting into a single whole all the structural subsystems of the type of troops of formations, formations and military units, directly to a separate reconnaissance and fire destruction means;
universality, which ensures the possibility of its operation in peacetime, a period of growing military threat and during the conduct of hostilities;
openness, which ensures the stability and adaptability of its structure to the reconfiguration of the structure of troops, as well as the possibility of expanding the range of tasks and functionality to be solved;
complexity of automation of the main management processes;
rational distribution of management functions between command posts, functional groups and headquarters officials;
a rational combination of centralized and decentralized management with consistent, by hierarchy levels, transit collection and transmission of information;
ensuring compatibility and interaction with other automated subsystems of the ACS of the Armed Forces;
the possibility of a phased creation and implementation of subsystems and elements of automated control systems in the troops and the inclusion of new elements in its composition.
The introduction of new information technologies in the subject area of the combat use of MFA should be based on a unified information, mathematical, algorithmic and software management tasks and provide:
adaptation of the information base to the subject area of the MFA and its integration into the combined arms system;
use along with standard mathematical models and methods for solving management problems, new methods for solving formalizable and insufficiently formalized tasks based on unified knowledge representation modules;
implementation of a unified ideology for solving management problems;
software synthesis m combination of models
subject area of R&A with formal models of control tasks.

Rice. 5. A variant of the structural-functional diagram of the automated control system for missile troops and artillery
Considering the issues of automating the M&A control system, attention should also be paid to the development of control machines. As an alternative, the following option can be proposed. Refusal to create specialized command and staff vehicles focused on specific tasks, and the transition to unified control vehicles (UMU), which have the same set of communications, data transmission and documentation. Their creation should be based on a wide application modern means information processing and new information technologies. This will allow, using common technological approaches, to develop a single CMU for all control units, which has identical CSA, differing only in sets of functional software and hardware modules. In the article, a functional software and hardware module of the KSA is understood as a set of software and hardware that perform a specific function.
Among the functional software and hardware modules of the KSA, one can single out modules used in all subsystems of the armed forces, and modules used in the functional modules of the KSA of missile and artillery formations, as well as in the intelligence subsystem. A variant of the functional software and hardware modules of the KSA R&A is shown in Figure 6.
Set of functional modules in local KLCA
The CMU should provide the ability to solve the following tasks:
setting to work as part of various control centers with the definition of exchange parameters with external subscribers;
receiving, processing, displaying and documenting orders, commands and combat control signals received from higher authorities, generating and issuing confirmations of received orders, signals and commands;
formation and issuance to subordinate (interacting) military command and control bodies (circularly and selectively) of orders, signals, commands and instructions, including target designations, receiving from them, processing and displaying confirmations of received orders, signals and commands, reports on the receipt and implementation of assigned tasks, other reports and reports;
priority processing of input information in accordance with the category of urgency;
formation and storage of forms (layouts) of formalized documents in the interests of officials of military command and control bodies;
collection, storage and issuance of formalized and non-formalized messages to communication channels with the maintenance of a document database and the ability to select the required document by catalog and request;
storage and display on the workstation of a digital map of the area with elements of the operational-tactical situation;
carrying out operational-tactical calculations and solving settlement problems in the interests of developing and making decisions;
input of data received from objects and sources that do not have a CSA;
control of the state of the components of the automated workplace and exchange paths (communication and data transmission channels) with external subscribers.

Rice. 6. A variant of the functional software and hardware modules of the missile and artillery automation systems

Rice. 7. Option of technical equipment of the unified control machine
It is proposed to use a domestic command and staff vehicle, mass-produced by enterprises of the Republic of Belarus, as the base vehicle for the UMU. It must have the same structure. technical means and differ only in flexible application software that implements control functions. The composition of automation, communications, life support and power supply of CMU is shown in Figure 7.
 The peculiarities of its automation tools include the fact that the workstation should be based on specialized personal computers, the printing device should be for general use, and one workstation should be implemented on the basis of a portable computer and used as a remote one. All workstations must be combined into a single network that has access to other UMUs within the control center LAN being created. In addition, all technical means connected to the system units (data transmission equipment, printing device and navigation equipment) must be used as network devices.
The peculiarities of its automation tools include the fact that the workstation should be based on specialized personal computers, the printing device should be for general use, and one workstation should be implemented on the basis of a portable computer and used as a remote one. All workstations must be combined into a single network that has access to other UMUs within the control center LAN being created. In addition, all technical means connected to the system units (data transmission equipment, printing device and navigation equipment) must be used as network devices.
AWS located in the operational compartment, according to their functional purpose, should be distributed as follows: AWP 1 - for functional control and information security, workstation 2 - server, workstation 3 - remote workplace and ARM 4 acts as a gateway and workstation of the network administrator.
This will unify and expand information, computing and maintenance services provided to officials, and to implement a modification series of machines that differ from each other only in the composition of the software.
The introduction of modern CSA into the practice of command and control of the MFA will ensure the effectiveness of the work of headquarters officials due to the multifactorial consideration of situational data and the reduction of time for solving control problems. The table shows a variant of the main time parameters for solving control problems that should be achieved as a result of automating the main processes of managing M&A.
Analysis of the experience of using automated control systems in Russian Federation and the results of scientific research conducted show that the practical use of automation in the process of command and control will increase the degree of implementation of the combat capabilities of the RV&A at the tactical level up to 15%, and at the operational level - up to 10%.
LITERATURE
1. Sinyavsky V. K. Problems of control of missile troops and artillery in modern operations// Science and military security. ~ 2004. - No. 1.
2. Sinyavsky V.K. Methodological aspects of decision support by officials of the headquarters of the missile troops and artillery // Science and military security.- 2005. - № 3.
3. Puzikov M.V. Development of theoretical provisions and development of practical recommendations on the combat use of missile troops and artillery of a regional grouping of troops (forces) in the air
operations in the Western theater of operations // Dis. cand. military sciences.- M: VAGSh. - 2005.
4 New technical solutions in the field of development of systems and means of automated control of the US Army. - M .. General Staff of the Armed Forces of the USSR, 6th Central Research Institute, issue No. 1721, 1989.- 108 p.
5. Kezhaev V.A., Chvarkov SV. Automated control systems, 4.2 / Fundamentals of automation of M&A control processes. - St. Petersburg: MO RF, 1999. - 74 p.
To comment, you must register on the site.
AT military history Great Britain, the word "Balaklava" is strongly associated with the cavalry attack of the British Light Brigade under the command of Lord Cardigan on the position of the Russian army during the Battle of Balaklava October 25, 1854 during the Crimean War. This attack was an example of a vain sacrifice, it was obviously doomed to failure. Historians are still arguing, exploring the reasons for this insane courage of the British cavalry.
Any military expert, having studied historical documents, will tell you that the main reason was the fuzzy command and control of the troops and the incorrect assessment of the combat situation. Lord Cardigan did not bother bringing information to his subordinates, setting specific tasks, he simply commanded: "Attack!". The attack was sudden for the Russian army, but it adequately met the enemy. The light brigade, having received a rebuff and retreating under the crossfire of Russian artillery, was completely destroyed.
After the Crimean War, the world military science has repeatedly revised the system of command and control in order to minimize such errors and ensure the maximum effectiveness of the combat use of troops. The effectiveness of any management system is determined by the result achieved, as well as at what cost it was obtained.
Modern high-tech weapons, training officers and soldiers for their use have become much more expensive over the past hundred years. Expensive equipment that is not always in service guarantees victory. This was well demonstrated by the Vietnam War, where the US army, which had modern weapons, was unable to defeat the inferior army of Vietnam and was forced to evacuate from Indochina.
The phrase “Winners are not judged” has long ceased to be a justifying criterion for evaluating the results of military operations, since the combat use of modern armed forces requires large expenditures from the state budget, often disproportionate to the results obtained.
History has shown that states that start a war and countries that defend their sovereignty face the same problems caused by resource hunger: in financial means, materials for the production of weapons, mobilization potential.
In this regard, the preparation and equipping of the armed forces by any state are presented with more high requirements which are getting tougher every year. “The task of the coming decade (for the Armed Forces of Russia), - said President of Russia Vladimir Putin, - is to ensure that the new structure of the Armed Forces can rely on fundamentally new technology. On equipment that "sees" further, shoots more accurately, reacts faster - than similar systems of any potential enemy. Our goal is to build a fully professional army.”
Building a professional army and creating effective system command and control are two interrelated tasks that should be based on general principles, ensuring the achievement of the set goals at the lowest cost, including in the course of real combat operations.
The main principles of command and control of troops are determined by the Ministry of Defense of the Russian Federation in the following form:
- unity of command;
- Centralization of management at all levels with the provision of subordinates with the opportunity to take the initiative in determining ways to perform the tasks assigned to them;
- Firmness and perseverance in implementation decisions taken; efficiency and flexibility in responding to changing conditions;
- Personal responsibility of the commanders (commanders) for the decisions made, the use of subordinate troops and the results of their fulfillment of the assigned tasks;
- High organization and creativity in the work of commanders (commanders), headquarters, and other bodies of military command and control.
I will draw your attention to points 2, 3 and 5, which, in my opinion, are among the key indicators in the art of command and control. In the modern Russian army, they began to be fully embodied starting from December 1, 2014, when National Defense Control Center of the Russian Federation (NTsUO RF) took up round-the-clock combat duty. The first "baptism of fire" NCUO RF received during the operation of the Russian Aerospace Forces in Syria.
It was the participation of the Russian Aerospace Forces in the destruction of the ISIS and Jabhat al-Nusra groups (both banned in the Russian Federation) that showed the correctness of the decision taken on May 8, 2013 by the President of Russia.
“The decision to create the NCUO was made by the President of Russia in order to improve the system of centralized management of the military organization of the state and the country's economy in addressing issues of preparation for the armed defense of the country. The National Center is, in fact, a mechanism operating around the clock to control all areas of the Armed Forces. It must ensure the ability and readiness of the troops to solve assigned tasks, the fulfillment of the state defense order, financial and material and technical resources, the recruitment of troops and training, the solution of medical and housing issues, our international activities, ”these words of Defense Minister Sergei Shoigu show how in practice the implementation of paragraph 2 of the principles of command and control was achieved.

In the previous 50 years, command and control of the Armed Forces (TsKP RF Armed Forces) was carried out by the Central Command Post of the General Staff. In modern conditions, the volume of information has increased many times over, the cycle of change in relevance has been reduced from weeks and days to hours and minutes. The information exchange of the Central Control Center of the Armed Forces of the Russian Federation, based on the timesheet of urgent reports with a low frequency of providing information in written documents (telegrams, reports, reports, and others), ceased to meet the requirements for information support for the leadership of the Ministry of Defense.
After taking up combat duty, the NTSUO of the Russian Federation actually minimized the decision-making time for a quick response to any situation. This is what ensured the success of the Russian Aerospace Forces in Syria.
Let me explain. For four years, the government of the Syrian Arab Republic, headed by Bashar al-Assad, and its army lost inch by inch the territory of their country to trained PMC instructors (USA, Turkey and some Arab countries) and equipped with modern weapons, communications and intelligence militant groups, including ISIS. The militants had time everywhere - they delivered effective strikes on military units, on defense positions, on military convoys and cities in Syria. The tactics of the groups were unpredictable, the captured settlements immediately turned into fortresses with a developed supply infrastructure and fortifications. Where the next breakthrough would occur, no one in the SAR army command could say with 100% certainty.
The fact is that in the actions of ISIS groups, the development of the doctrine of "network-centric war" (Eng. Network-centric warfare) of the US Army, which they began to develop in 1998. The main principle of warfare in a "network-centric war" is the creation of so-called "packs" (armed groups), followed by enemy attacks in all directions with the help of small units.
This is the concept of warfare, which provides for an increase in the combat power of a grouping of joint forces through the formation of an information and switching network that combines sources of information (intelligence), command and control facilities and means of destruction (suppression), ensuring that participants in operations receive reliable and complete information about the situation in real life. time.
Network-centric warfare (NCW), according to the authors, is capable of waging only highly intelligent forces. Such forces, using the knowledge gained from comprehensive surveillance of the battlespace and an expanded understanding of the intentions of the command, are capable of greater efficiency than when conducting autonomous, relatively fragmented operations.
ISIS groups were only a tool in the war against the government of Bashar al-Assad, control through the ACCS and coordination of the fighting of these groups was most likely provided by PMC contractors and hundreds of military instructors stationed in Turkey, Kuwait and Iraq.
The NCW doctrine provides for four main phases of warfare.
- Achieving information superiority through the advance destruction (disabling, suppression) of the enemy’s intelligence and information support system (reconnaissance assets and systems, network-forming nodes, information processing and control centers)
- Gaining superiority (dominance) in the air by suppressing (destroying) the enemy's air defense system.
- The gradual destruction of enemy weapons left without control and information, in the first place missile systems, aviation, artillery, armored vehicles.
- The final suppression or destruction of pockets of enemy resistance.
Whether the SAR army had the opportunity to resist hostilities on the basis of the NCW doctrine, the answer is obvious. Therefore, the Russian Aerospace Forces really turned this “hopeless” situation, since they coordinated and controlled their military operations from a single center for the ACCS of the RF Armed Forces, in which all information on the theater of operations in Syria was collected. In addition to combat missions, the NCUO of the Russian Federation centrally and in parallel solved all issues related to the supply and deployment of our group of armed forces at the Khmeimim and Tartus bases, reducing logistics operations to minimal costs. Do not forget about informing the world media about the course of hostilities with the provision of exclusive personnel from air and space reconnaissance.
Is it possible to call the Russian automated command and control system of the RF Armed Forces and the NTsUO RF on combat duty a response to the NCW doctrine? Yes and no.
It is easier to consider this comparison according to the "as is" criterion.
ACCS of the US ARMY.
The NCW doctrine, launched in 1998, was first applied in practice in the war with Iraq in 2003. The technical basis of this doctrine was two US Army ACCS - the combat planning and aviation control system in the theater - TVMSS ( Theater Battle Management Core Systems) and FBCB2 combat control information system ( Force XXΙ Battle Command Brigade or Below), covering tactical command along the brigade-battalion-company hierarchy.

The FBCB2 terminals were located on board tanks, infantry fighting vehicles, armored personnel carriers, self-propelled guns, rocket launchers and multi-purpose off-road vehicles of the line units of the US Army and Marine Corps. They were connected to a two-layer radio communication network, including the EPLRS/SINCGARS air-ground segment and the INMARSAT space segment. Data exchange was carried out within the virtual network of the tactical Internet.
Thus, the commanders of the forward units of American divisions on the battlefield were given the opportunity to interact directly with artillery units and tactical, and in some cases, strategic aviation.
The actions of the Iraqi army were practically paralyzed by the situational awareness of the American troops at an early stage about the transfer and accumulation of the forces of the defenders. A typical example is the operation to seize a large bridge in the southeast of Baghdad.
In the reports provided to the US Army command, this operation is characterized as “repelling an attempted night counterattack by two brigades of the Republican Guard, supported by 70 tanks, on the bridgehead of one battalion of the 3rd Mechanized Division, reinforced by 10 Abrams tanks and 4 Bradley infantry fighting vehicles, in urban areas of Baghdad. Having stumbled upon a bombing strike and artillery fire even before the start of the counterattack and having lost half of the personnel killed and wounded in dense pre-battle formations, the Iraqis were forced to retreat.
In fact, the ACCS failed because it could not detect the advancing Iraqi brigades in a timely manner. Before the start of the operation, intelligence carefully studied the photographs received from satellites, reported that the bridge was not guarded and no enemy troops were observed in the vicinity. Therefore, the appearance of Iraqi units for the American battalion was a complete surprise, delaying the completion of the combat mission by almost a day. Only absolute air supremacy and superior firepower saved the Americans from defeat.
In general, during the campaign in Iraq, the combined ACCS turned out to be ineffective due to the low bandwidth of information channels, so the units of the US Army and the Marine Corps often switched to traditional means of communication. As a result of the war in Iraq, the ACCS was sent for revision, and until then it was recommended for use against enemy irregular forces ..
After the war in Iraq, the promising ACCS underwent a comprehensive revision in accordance with the program Joint Battle Command Platform. It includes information docking of ACCS systems of the ground forces, air defense, aviation and navy using the DIB (DCGS Integrated Backbone) software interface and equipping them with FBCB2 terminals. In the space and air segment, the transition to broadband is being completed. Operations in Libya and the war in Syria show the direction of further improvement of this ACCS in practice
Currently, this system operates in parallel with the HART (Heterogeneous Airborne Reconnaissance Team) multispectral reconnaissance network, which has a UAV flight fleet of 7,400 units.
Separate from the ACCS is the United States Cyber Command (USCYBERCOM), which plans, coordinates, integrates, synchronizes and conducts operations management and protection activities. computer networks US Department of Defense. Also standing apart is the United States Strategic Command (USSTRATCOM), which combines the management of strategic nuclear forces, missile defense and military space forces.
Thus, there is no need to talk about the current unified automated command and control system in the US Army. The only advantage in command and control of the US Army is the INMARSAT (11 geostationary satellites) and IRIDIUM (66 satellites orbiting the Earth in 11 orbits at an altitude of about 780 km), which allow for operational strategic management US troops at a great distance, minimizing delays in the passage of information.
ACCS OF THE ARMED FORCES OF RUSSIA
This is the first in the world a unified command and control system for all military units that are part of the structure of the Russian Armed Forces, including the nuclear triad, implemented in the current National Defense Control Center of the Russian Federation and the corresponding centers of subordinate control bodies: military district (operational-strategic command) - army - division (brigade).

The technical basis of the ACS of the Armed Forces of the Russian Federation is the Akatsia-M automated command and control system (ACCS) of domestic production, which has a mobile analogue in the troops (MCH ACS R Akatsia-M), which has been in service with the Russian military districts since 2005. ACS "Acacia-M" allows military personnel to be in the same information space, both in places of permanent deployment (NTsUO and Control Centers for the troops of the districts), and when going out into the field or during combat operations. In fact, Akatsia-M is a military analogue of the Internet. The software on which the ACCS runs is designed for standard forces and controls, as well as standard combat crews.
ACCS "Acacia-M" in combination with their deployed mobile versions, they provide operational-strategic and operational control of the Russian Armed Forces.
Operational-tactical and tactical command and control of troops is carried out by complexes of the Unified Tactical Level Control System (ESU TK) "Constellation-M2" and ESU OTZ "Andromeda-D".
ESU TZ "Constellation-M2" is being tested and further improved in the Ground Forces, and ESU OTZ "Andromeda-D" in the Airborne Forces. These complexes were tested during numerous combined arms exercises and surprise inspections that the Russian Armed Forces conducted in 2015, as well as in real combat conditions during the operation of the Russian Aerospace Forces in Syria.
All information flows from the ACCS are concentrated in the "Stavka of the Supreme High Command" - NCUO RF. PAK NCUO operates an information system based on the Astra Linux operating system manufactured by the company "RusBITech", and the provision of geospatial information is based on the concept of geographically distributed collection, storage and delivery of geospatial data (full name - EASO Armed Forces of the Russian Federation GPI) developed Groups "Kronstadt".
The National Center is based on three control centers:
- The Strategic Nuclear Forces Control Center (SNF) is designed to control the use of nuclear weapons by decision of the country's top military-political leadership;
- Combat control center monitors the military-political situation in the world, analyzes and forecasts the development of threats to the Russian Federation or its allies. It also provides control over the use of the Armed Forces, as well as troops and military formations that are not part of the structure of the Russian Ministry of Defense;
- Day to day operations management center, leading monitoring of all activities military organization states concerning the comprehensive provision of the Armed Forces. He also coordinates the activities of federal authorities to meet the needs of other troops, military formations, bodies and special formations that are not part of the Ministry of Defense.
The next stage of work involves scaling these information technologies down the structure of the armed forces to the headquarters of formations and tactical units, while maintaining the basic principles of the system architecture and specific software and hardware solutions for monitoring the situation, decision support and other elements of command and control of troops and forces that have been tested in the NTSUO.

In the course of "field tests" during exercises and combat use in Syria, the ACCS of the RF Armed Forces showed the following results:
- A high efficiency of information exchange was achieved (collection, processing and display of information about the tactical situation), which increases the speed of performing the main control tasks by 5-6 times, compared with manual control systems.
- Due to the constant collection of data on the situation in the round-the-clock monitoring mode, the continuity of the operation of the entire ACCS of the RF Armed Forces was ensured from the operational-strategic level (NTsUO) to the tactical level (ESU TK).
- As a result of the use of unified hardware and software systems (HSC), unified software (including for graphical display of situational data) for all levels of command from the soldier to the commander of the Armed Forces, a high degree of unification of the elements of the command and control system was achieved.
- The survivability of the ACCS was tested in the event of a failure of the APC group (headquarters with the APC), which, thanks to the ability of the ACCS to quickly restore its performance, including in a distributed mode, showed a high degree the reliability of the means and elements of the complexes used.
Russian space constellation of military communications and intelligence satellites on this moment inferior to the American groups INMARSAT, IRIDIUM and reconnaissance satellites of the National Reconnaissance Office (NRO).
With the commissioning of the spacecraft of the Unified Space System and other types of military and dual-use spacecraft, the RF Armed Forces will reach the advanced world level in this segment as well.
Alexey Leonkov
Military expert of the Arsenal of the Fatherland magazine
Historical overview
Over the past 30 years, several automated combat control systems for the Ground Forces (ACCS) have been created in the USSR, the USA and Russia - Manevr, AGCCS, ATCCS, FBCB2, Akatsia-M, ESU TZ and Andromeda-D. They had a different scope of implementation of the functions of command and control, but coincided with each other in the general approach to automation.
ACCS illustration
These systems were created in the image and likeness of the hierarchical organizational and administrative structure of the Ground Forces. From a technical point of view, being software and hardware systems, automated systems multiplied the shortcomings of this structure:
- the vulnerability of the entire system in case of failure of the upper level;
- the absence of horizontal ties between the various branches of the armed forces;
- reduced speed of information passing between units of the same level, forced to communicate with each other through the upper level.
The development of systems was also carried out in a hierarchical sequence - first, the functional composition of the upper level was implemented, then the middle one, and only then the lower one, and the priority of the completeness of the implementation of functions was determined in the same sequence. As a result, ACCS were built on the basis of the same type of centralized architecture:
— top-level automated control center;
— mid-level automated control centers;
- lower-level automated control centers.
It can be seen from this scheme that the fire control systems (FCS) of tanks, infantry fighting vehicles, self-propelled artillery and rocket launchers, air defense / missile defense systems, as well as information and control systems (ICS) of reconnaissance equipment were not included in the ACS.
The development of ACS was carried out with a lag in the development of the basis for command and control - communications. The creation of many multi-level automated control centers resulted in an intensive information exchange between them, which significantly increased the need for bandwidth of communication channels. The situation was aggravated by the mobile nature of the centers of the lower level, requiring a fundamentally new solution in the field of radio communications.
Initially, it was clear that the information exchange will consist not only and not so much of voice communication, but will include the transmission of data, graphics and streaming video. The formats of digital, textual, graphic and video information must be compatible with the on-board control systems of numerous types of weapons and instrumental reconnaissance. At the same time, the method of information exchange in a combat situation must withstand the failure of some of the relay nodes and communication channels. These circumstances imposed stringent requirements for the unification of information exchange rules, which were not fully implemented in any of the ACCS.
This was due to the limitation of goal-setting at the stage of developing concepts, setting goals and prioritizing the creation of systems. Since the automated control centers were to be located at the level of headquarters of military formations, units and divisions, the capabilities of the automated control system were limited to information functions:
- planning of military operations.
In contrast to the combat information and control systems of air defense / missile defense systems, ships of the Navy and weapons control systems of combat vehicles, the automatic control system did not have the function of controlling the fire of subunits, units and formations directly on the battlefield. The implementation of the ACCS functionality within the framework of automated control centers made the system extremely vulnerable if any of them failed. Even without taking into account this risk, the acceleration of the decision-making process at the headquarters level had too little impact on the direct management of combat operations in the form of a decrease in the reaction time to the changing operational-tactical situation of a military unit, unit or subunit.
Choice of ACCS 2.0 target
The purpose of creating an automated system should be to reduce the period of time between the moment the enemy is detected and the moment he is defeated. The interaction of direct participants in hostilities should take place on a two-way basis "forward unit - fire support unit" in real time. The main type of interaction is the transmission of the coordinates and type of the target over the communication channel and the response fire on the target.
ACCS 2.0 is based on a distributed service-oriented architecture without the formation of automated control centers. All combatants are equipped with wearable communicators with built-in transceivers. Communicators contain full-featured software and digital maps of the area. On-board FCS of combat vehicles, aircraft and artillery, missile and anti-aircraft systems (hereinafter referred to as the FCS of combat vehicles) and IMS of reconnaissance equipment, also equipped with transceivers, contain specialized software and digital terrain maps. The hardware and software complexes (HSC) of headquarters are equipped with transceivers and contain specialized software with limited functionality.
Communicators, OMS, IMS and HSC are connected to a single communication network as subscriber terminals. Information interaction between them is carried out in the form of tactical data exchange. Full-featured automated control at the company level and below is provided with the help of communicators, at the battalion level and above - with the help of communicators and remote access to the agro-industrial complex according to the "client-server" scheme
The source of tactical data is the communicators of the infantrymen, the IMS of technical reconnaissance equipment and the OMS of combat vehicles. The processing of tactical data is carried out in the following order:
- primary target designation is carried out with the help of infantrymen's communicators and IUS of technical reconnaissance equipment;
- adjustment of the primary target designation (if necessary) is carried out using communicators of the command staff of the squad level and above;
- target distribution is carried out with the help of the SLA of artillery, missile and air defense systems;
- hitting targets is carried out with the help of the FCS of combat vehicles.
Generalization of tactical data is carried out at each command level using communicators (squad-platoon-company), as well as communicators and APC (battalion and above). Generalized tactical data is transmitted to the upper and lower levels of management to provide situational awareness. Combat planning is carried out similarly to the process of summarizing tactical data.
As a result, the structure of ACCS 2.0 takes the form of a Grid-system, in the nodes of which there are communicators, OMS, IMS and HSC, interconnected:
- vertically by the hierarchy of the organizational military structure;
- horizontal exchange of tactical data.
 grid system
grid system
Setting tasks for ACCS 2.0
Connection
Despite the fact that the military communications system is self-sufficient, the ACCS 2.0 project must be coordinated with the development of its new version, which has a large bandwidth and high fault tolerance.
At present, the main method of transmitting information in the military sphere is HF and VHF radio communications. The increase in radio capacity is achieved by switching to higher frequencies than those already in use. The decimeter range of radio waves is used for cellular telephone connection. Therefore, ACCS 2.0 will need to use the centimeter range with a frequency of 3 to 30 GHz (microwave communication). Radio waves of this range propagate within the line of sight, but are characterized by strong attenuation when passing through vertical obstacles such as building walls and tree trunks. To bypass them, microwave communication repeaters must be placed in the air on board the UAV. In order to minimize dark areas, the maximum angle of inclination of radiation to the ground surface should not exceed 45 degrees.
The air segment of the microwave communication network is intended for use in the combat zone. For communications services for reconnaissance operations behind enemy lines, it is necessary to use the space segment of microwave communications. It is advisable to exchange information between stationary objects in your rear using a wired communication segment operating in the optical frequency range of the electromagnetic spectrum. The presence of the air segment does not exclude the use of portable ground-based short-range microwave repeaters used in combat operations inside premises with radio-tight ceilings.
 Communication scheme
Communication scheme
To maintain constant radio contact in the air segment of the microwave communication network, it is required to abandon the existing trunk scheme "one base station - many subscriber transceivers" and switch to the zone scheme "many node stations - many subscriber transceivers". Nodal stations - repeaters should be placed at the topological network vertices with triangular cells (cells). Each node station must provide the following functions:
- channel switching at the request of subscribers;
— retransmission of signals between subscriber transceivers;
— relaying of signals between network zones;
— relaying signals from/to stationary subscriber transceivers serving as gateways for the wired segment of the communication network;
— relaying of signals from/to the space segment of the communication network.
Depending on the UAV class, the height of the nodal stations above the ground will be from 6 to 12 km. At the maximum radiation inclination angle, the communication service radius will be in the same range of values. In order to mutually overlap service areas, the distance between nodal stations should be halved from the maximum. Thus, high fault tolerance of the network is achieved by sevenfold redundancy of node stations. An additional degree of fault tolerance of microwave communications is provided by deploying UAV repeaters only over its territory and covering network nodes with the help of short-range air defense / missile defense systems.
 DarkStar - UAV repeater with microwave PAR
DarkStar - UAV repeater with microwave PAR
Noise immunity is achieved by using CDMA wideband channel coding technology, which features a noise-like signal spectrum, support for dedicated data/voice channels, or multiple channel aggregation for video streaming. The signals reflected from natural obstacles are added to the main signal, which increases the noise immunity of the system. Communication with each subscriber is supported by at least two beams, allowing the subscriber to transfer between different nodes and network zones without losing connection. The use of narrowly directed radiation makes it possible to reduce the radio visibility of transceivers and determine the location of network subscribers with high accuracy.
Technologies, protocols and formats of information transfer
All information in the communication network serving ACCS 2.0 is transmitted in digital form. In order to provide a multi-service mode of operation, it is proposed to use MPLS technology based on the assignment of unified labels to information packets, regardless of the transport protocol that supports the transmission of information of a certain type. Labels address information through the end-to-end channel and allow you to set the priority of transmission depending on the type of information and message address.
The microwave communication network uses the WCDMA channel protocol with code division and spread spectrum of signals, the power of which can be less than the power of the radio background, which, combined with the wideband nature of the signals, makes it possible to reuse the same frequency band in neighboring areas of the network.
 CDMA spectrum
CDMA spectrum
In the wired segment of the network, it is proposed to use the Ethernet channel protocol with code division of channels, the latest version of the standard of which provides information exchange in duplex operation mode without aggregation over one optical fiber at a speed of 25 gigabits per second, with aggregation over four optical fibers at a speed of 100 gigabits per second . In this case, the distance between communication nodes / signal amplifiers can reach 40 km.
As switches in network nodes, it is necessary to use routers that control the composition of the network using the OSPF dynamic routing protocol. The protocol supports automatic reconfiguration of zones, nodes and channels in case of failure of some routers.
At the network level, the IP protocol is used, which ensures guaranteed delivery of information messages consisting of individual packets along any of the possible routes passing through network nodes and connecting two or more subscribers. Communication is interrupted only in case of failure of all network nodes.
Transport protocols for the transfer of information of a certain type are standard solutions tested on the Internet:
- TCP data transfer protocol;
— voice transmission protocol VoIP;
- RTP video streaming protocol.
It is proposed to use HTTP with the MIME extension as an application data transfer protocol. Presentation formats include HTML (text), JPEG (photos), MID/MIF (map data), MP3 (audio), and MPEG (video).
Functional composition of ACCS 2.0
ACCS 2.0 should ensure the transition from an information system to a management system that implements the following functions:
- situational awareness of the operational-tactical situation;
- planning of military operations;
- Combat management.
Situational awareness is provided by real-time integration of all available information about the deployment of military personnel and military equipment that are part of their own unit, neighboring units, as well as the enemy forces:
- the location of the military personnel of their own unit, equipped with communicators, combat vehicles equipped with FCS, and technical intelligence equipment, equipped with IMS, is taken by UAV repeaters;
- the location of troops and weapons of neighboring units is transmitted from the upper level of ACCS 2.0;
- the location of enemy firing points and combat vehicles on the battlefield is determined by the infantrymen in the process of target designation using communicators, as well as by the crews of combat vehicles using the FCS;
- the location of the enemy troops and weapons in his rear is recognized by the operators of technical reconnaissance equipment with the help of IUS.
 Digital battlefield
Digital battlefield
Combat planning is carried out according to one of two options:
- operational planning of the needs for ammunition, fuel and food according to the actual consumption during the hostilities;
— advanced planning combat operations with the definition of the deployment line, the offensive zone, the final object, fire support forces, etc.
Operational planning of needs for material and technical supply is carried out with the help of communicators, long-term planning of combat operations - with the help of the agro-industrial complex.
Control of the actions of subunits directly during the battle is carried out in real time by receiving voice and video information, giving voice instructions to subordinate military personnel, as well as using:
- adjustments to the primary target designation of advanced units with a change in the priority of hitting selected targets;
- adjustments to the primary target distribution of fire support units with a change in the type of weapon, type of ammunition, firing sectors, etc.
In addition, the infantryman's communicator software must provide the functions of a wearable weapon control system to minimize the amount of equipment that is part of the equipment of military personnel. The communicator serves as an SLA for assault and sniper rifles, machine guns, rocket and automatic grenade launchers. Pointing the weapon at the target is carried out by combining the line of sight of the sighting devices with the virtual projection of this line, calculated by the processor, taking into account the coordinates, range and speed of the target.
ASUV 2.0 infantry communicator
The infantryman's communicator is designed for individual equipment of privates, sergeants, officers and generals of the Ground Forces. It is made in the form of a pocket device with a sealed case, inside which are the processor, RAM, read-only memory, battery, radio modem, ports for connecting an external antenna and information display device, fiber optic line input and an electrical connector for recharging the battery. In addition, the communicator contains modules of the global satellite positioning system and autonomous inertial orientation system.
 dome antenna
dome antenna
The communicator is equipped with an external antenna in one of two options:
— omnidirectional whip antenna;
- a narrowly directed active phased antenna array (AFAR), which forms a tracking radio beam in the direction of the UAV relay of the air segment of microwave communications or the orbit of the satellite relay of the space segment of microwave communications.
The whip antenna mounts directly into the communicator port connector and is designed for wireless communication inside a shielded room. Complete with a whip antenna and a low-power airborne microwave repeater, the communicator ensures the distributed work of unit commanders and headquarters operators located at mobile command posts and on board command vehicles, helicopters and aircraft.
APAA is made in the form of a dome shell formed by a flexible printed circuit board, on the front side of which there are radiating elements, on the reverse side - a shielding metal coating. The dome shell is inserted inside the infantryman's polymer helmet and connected to the communicator using a fiber optic cable connecting the bidirectional optoelectronic converters. AFAR is designed for mobile radio communication with automated control centers, other communicators and the control system of combat vehicles.
 HEADLIGHTS on a printed circuit board
HEADLIGHTS on a printed circuit board
The AFAA tracking beam makes it possible to reduce the radiation power of the antenna by an order of magnitude, eliminate the radio visibility of transmitters and provide microwave repeaters with the possibility of spatial selection of radio beams and sources of interference created by the enemy using electronic warfare.
The information display device consists of projection glasses, vibrating speakers/microphones that transmit sound through the bone tissue of the skull, and a fiber optic cable connecting the communicator port to the projection glasses. The port houses bidirectional optoelectronic converters. Projection glasses consist of a frame, protective lenses, prism projectors, external and internal lenses.
Vibrating speakers/microphones contain bi-directional optoacoustic transducers. The image is transmitted in three ranges of the optical spectrum - visible from optoelectronic converters to projectors, near infrared from optoelectronic converters to internal lenses and vice versa, and also in far infrared from external lenses to optoelectronic converters. The sound is transmitted in the form of modulated infrared radiation between optoelectronic and optoacoustic transducers.
 Projection glasses
Projection glasses
The thermal image of the terrain, received by external lenses and processed by the processor, is converted into a visible one and projected onto the inner surface of the protective lenses of the projection glasses, including with magnification. At the same time, the thermal image is combined with a digital topographic map stored in a read-only memory device for orientation in the area and determining the coordinates of targets. Tactical signs, reticle, virtual buttons, cursor, etc. are projected on the surface of protective lenses. Infrared radiation reflected from the pupils of the eyes serves to position the cursor in the field of view. The communicator is controlled using voice commands and hand gestures.
Combat vehicle crew members are also equipped with communicators that connect to the onboard FCS via an internal wired communication line. Outside the combat vehicle, wireless communication between crew members is provided using domed AFARs built into protective helmets.
 Digital map of the area
Digital map of the area
ACCS 2.0 hardware and software
Information Security
Protection of information in communication channels should be ensured using symmetric encryption and private key technology, which are regularly replaced with new ones using asymmetric encryption and public key technology.
The processors of infantrymen's communicators, control systems of combat vehicles, IMS of technical reconnaissance equipment and agro-industrial complex of headquarters must have unique identification numbers taken into account in the information encryption algorithms, which allow blocking communication in case the equipment falls into the hands of the enemy.
ACCS 2.0 equipment must maintain a radio monitoring mode for its location (by direction finding of emitted radio signals using UAV repeaters) and the physical condition of military personnel carrying the equipment (by monitoring breathing with vibration microphones). In the event that the equipment falls into the hands of the enemy or the wearer of the equipment loses consciousness, communication is blocked.
Hardware
The ACCS 2.0 hardware should be produced on a domestic element base using certified imported components. To minimize power consumption and heat dissipation, hardware should use multi-core processors and solid-state persistent storage devices.
To protect against high power electromagnetic pulses, electronic equipment and external power supplies are placed in sealed metal cases with conductive cooling. Power cables are shielded with a metal braid. Fuses in the form of avalanche-span diodes are mounted in external electrical connectors. Wired communication lines are made of optical fiber. External recording devices are equipped with bidirectional optoelectronic converters connected to the equipment in the same way as wired communication lines.
The sources of electricity are high-capacity lithium-ion batteries recharged from on-board generators of combat and transport vehicles.
The computing power of the equipment must ensure its multiple redundancy according to the following scheme:
- when the communicator of the top-level unit commander is out of order, its functions are automatically transferred to the communicator of the deputy unit commander (in the case of an infantry unit, to one of the infantrymen);
- when the communicator of the deputy unit commander is out of order, its functions are automatically transferred to the communicator of one of the commanders of the lower-level unit;
- when the agro-industrial complex of the headquarters of the upper-level unit is out of order, its functions are automatically transferred to the agro-industrial complex of the headquarters at the reserve command post;
- in case of failure of the APC of the headquarters at the reserve command post, its functions are automatically transferred to the APC of the headquarters of one of the subdivisions of the lower level.
Software
ACCS 2.0 software should be developed in accordance with computer and communication technologies, data transfer protocols and information presentation formats that meet international standards.
System software, including the input-output system, operating system, file system and database management system, should consist only of domestic software products in order to exclude unauthorized access to information, interception of control and disable software and weapons.
Application software may contain both domestic and imported components, provided that the latter are supplied with an open source code and a description of the block diagrams of the algorithms used.
Design and commissioning of ACCS 2.0
Creation questions Russian production element base and interstate cooperation in the production of ACCS 2.0 components are within the competence of the Military-Industrial Commission under the Government of the Russian Federation.
Concept development, task setting, approval single list technologies, protocols and data transfer formats, it is advisable to entrust the project team under the leadership of the Minister of Defense of the Russian Federation.
To coordinate the activities of organizations developing regulations, hardware, algorithms and software for communication and computer systems, as well as to ensure the subsequent functioning of ACCS 2.0 under the command of the General Staff of the RF Armed Forces, it is necessary to create an operational command similar to the United States Cyber Command.
When putting ACCS 2.0 into service, its functionality should be provided at the C4ISR level (Command, Control, Communications, Computers, Intelligence, Surveillance, Reconnaissance). At the same time, the level of automated control at the tactical level must correspond to the Digital Battle Field technology.
/Andrey Vasiliev, especially for the "Army Bulletin"/
The command of the RF Armed Forces is making significant efforts to ensure that the operational leadership links ensure fast, stable, reliable, continuous and flexible command and control of the Armed Forces, both in peacetime and in wartime.
At the same time, a large role is given to the automation of command and control of combat forces, which is based on the following principles:
1. The introduction of computer technology in all control bodies of strategic, operational and tactical levels.
2. Integrated automation processes for managing the combat activities of troops.
3. Availability of developed communication systems that allow to quickly and reliably transfer data on a global scale and organize communication in new areas.
These principles find practical implementation in automated command and control systems (ATCS), which ensure the collection, transmission, processing and presentation to the commander of the information necessary for command and control of troops in the preparation and conduct of combat operations, as well as bringing the decisions made to the troops.
ACCS is used to automate work command posts and control bodies related to the combat support of the troops. The object of control of these systems are combat forces.
In the daily management of troops, ACCS are used to solve such problems as:
Development of the basic concepts of building the Armed Forces;
Evaluation of current operational plans for the combat use of troops;
Simulation of combat situations;
Ensuring the combat readiness of troops (material and technical support, transportation, accounting of personnel, etc.);
Planning and conducting mobilization deployment;
Assessment of the combat capabilities of a potential enemy;
Evaluation of the effectiveness of existing and prospective weapons systems and development of requirements for them;
Implementation of control and financial operations;
Provision of research work.
Consider the principles of construction and purpose of automated command and control systems (ACCS).
ACCS – it is a man-machine system that provides a high level of operational command and control of troops both in peacetime and in wartime for all types of combat operations.
The introduction of ACCS into the work of command and control bodies is carried out in order to increase the stability, continuity, efficiency and secrecy of command and control, as well as the effective use of their combat capabilities in solving tasks in battle.
The automation of command and control of troops implies the use of modern computer technology and various high-performance technical devices collection, accumulation, processing and transmission of information together with the relevant information, mathematical and software.
The technical basis for the automation of troop control is made up of various computers with devices for input and output of information, equipment for displaying and documenting it, as well as telecode receiving and transmitting communication equipment, etc.
The basic principles of building an automated control system include:
1. A systematic approach to the development and implementation of ACCS.
2. Automation of a wide range of command and control tasks.
3. Development and implementation of new methods for collecting, accumulating, processing and transmitting information.
4. Opportunity to develop and build up ACCS .
By belonging to different levels of management, ACCS are divided into strategic ones; operational-strategic; operational and tactical.
By types of troops, ACCS are divided into combined arms, types of troops, special forces, rear, technical support, etc.
In our army in the 90s of the twentieth century, the ACS "Maneuver" was developed and implemented in the troops.
ACS "Maneuver" was intended for:
Collecting data about own troops and enemy troops;
Putting this data on maps;
Statement of combat missions;
Transmission of commands (signals) and confirmation of receipt of these commands, etc.
ACS "Maneuver" was a special unit, including a set of command and staff vehicles (KShM) and special vehicles (SM).
So the combined arms subsystem of the division's ACCS included 13 KShM and 1 SM. The rocket troops and artillery had 8 KShM and 1 SM. Aviation and air defense had 2 KShM and 1 SM.
There were 12 KShM and 1 SM per tank division. The tank regiment was given 3 KShM.
The command and staff vehicle contained:
Specialized on-board computer;
Data transmission equipment;
Alphanumeric equipment;
Console for dialing formalized codegrams;
Coordinate reading device;
Drawing and graphic apparatus;
TV board;
Alphanumeric printer;
interface devices;
life support system, etc.
Consider the principles of building automated command and control systems in the United States.
According to the foreign press, in the United States and other countries of the NATO bloc, intensive automation of command and control of troops at the operational-tactical level is underway.
The existing automated control systems are divided into three main categories according to the principles of construction, which are determined by the specifics of the work of the relevant governing bodies.
These are the command and control systems of the top military leadership, the ministries of the branches of the armed forces and the joint commands in the zones. Their characteristic feature is the coverage of the governing bodies of the same rank without connecting the lower levels, that is, the focus on solving problems in the interests of this level of management.
Control systems for strategic offensive and defensive forces can serve as an example of such automated command and control systems, where, in order to ensure high efficiency, direct transmission of commands and orders of the commander-in-chief to individual aircraft or launchers is provided.
In the ACCS of the third category, the centralized and decentralized principles of construction are combined together. Systems are a set of automated control centers, each of which is able to solve problems in the interests of both its own and lower levels.
A similar principle is applied when creating an automated control system for the operational-tactical level. Such systems must be particularly flexible and quickly adapt to the specific conditions of the combat situation.
As examples of the concrete implementation of these principles, let us consider automated control systems of the top military leadership, strategic aviation command and ground forces.






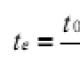



Only lovers will survive
Features of advertising aimed at children
retouching old photos in photoshop retouching old photos
What is an NPO: decoding, definition of goals, types of activities Does a non-profit organization have the right
Gleb Nikitin First Deputy