Here you will find definitions for such concepts as: vishing, gambling, griefers, cyberbullying, gambling addiction, sexting and other words that the built-in Windows dictionary "know" not soon. The dangers of the Internet are evolving much faster than software.
2 . . An extensive and detailed guide on how to install software on a computer or laptop that does not allow a child to see content (information) that is dangerous for him. And also in this document "Teaching children the basics of safety when working with the Internet."Internet safety note
Every year there are more young people on the Internet, and schoolchildren are among the most active users of Runet. Meanwhile, in addition to a huge number of opportunities, the Internet also brings problems. This memo is to help you stay safe online.Computer viruses
A computer virus is a type computer programs, a distinctive feature of which is the ability to reproduce. In addition to this, viruses can damage or completely destroy all files and data controlled by the user on whose behalf the infected program was launched, as well as damage or even destroy operating system with all files in general. In most cases, viruses are spread via the Internet.
Anti-malware methods:
- Use modern operating systems with a serious level of protection against malware;
- Constantly install patches (digital patches that are automatically installed to improve the program) and other updates to your operating system. Download them only from the official website of the OS developer. If there is an automatic update mode, turn it on;
- Work on your computer as a user, not an administrator. This will prevent most malware from being installed on your personal computer;
- Use antivirus software products well-known manufacturers, with automatic database updates;
- Restrict physical access to the computer for unauthorized persons;
- Use external media, such as a flash drive, disk or file from the Internet, only from qualified sources;
- Do not open computer files received from unreliable sources. Even those files that your friend sent. Better ask him if he sent them to you.
WI-FI networks
Wi-Fi is not a type of data transmission, not a technology, but just a brand, a brand. Back in 1991 Dutch company registered the brand "WECA", which meant the phrase "Wireless Fidelity", which translates as "wireless precision". Another abbreviation has reached our time, which is the same technology. It is an abbreviation for Wi-Fi. This name was given with an allusion to the Hi-Fi standard of the highest sound technology, which means “high fidelity” in translation.
Yes, free Internet access in cafes, hotels and airports is a great opportunity to get online. But many experts believe that public Wi-Fi networks are not secure.
Security Tips for Using Public Wi-Fi Networks:
- Do not share your personal information over public Wi-Fi networks. When working in them, it is advisable not to enter access passwords, logins and some numbers;
- Use and update your antivirus software and firewall. Thus, you will protect yourself from downloading a virus to your device;
- Turn off File and Printer Sharing when using Wi-Fi. This function closed by default, but some users activate it for ease of use at work or school;
- Do not use public WI-FI to transfer personal data, for example, to access social networks or e-mail;
- Use only a secure connection via HTTPS, not HTTP, ie. when typing a web address, enter exactly “https://”;
- Turn off "Connect to Wi-Fi automatically" on your mobile phone. Prevent your device from automatically connecting to Wi-Fi networks without your consent.
Social networks
Social networks are actively entering our lives, many people work and live there permanently, and a billion people are already registered on Facebook, which is one seventh of all the inhabitants of the planet. Many users do not realize that the information they post on in social networks, can be found and used by anyone, including not necessarily with good intentions.
- Limit your friends list. You should not have random and unfamiliar people in your friends;
- Protect your privacy. Do not provide passwords, phone numbers, addresses, your date of birth or other personal information. Attackers can even use information about how you and your parents plan to spend your holidays;
- Protect your reputation - keep it clean and ask yourself: would you like other users to see what you upload? Think before you post, write and upload;
- If you are talking to people you do not know, do not use your real name and other personal information: name, place of residence, place of study, etc.;
- Avoid posting photos on the Internet that show you in an area that can be used to determine your location;
- When registering on a social network, you must use complex passwords consisting of letters and numbers and with at least 8 characters;
- You must use different passwords for the social network, mail, and other sites. Then if you get hacked, then the attackers will get access to only one place, and not all at once.
Electronic money
Electronic money is a very convenient payment method, but there are scammers who want to get this money.
Electronic money appeared quite recently and it is because of this that in many states it is still not spelled out about them in the laws. In Russia, they function and they are already spelled out in the law, where they are divided into several types - anonymous and not anonymous. The difference is that anonymous ones are those in which it is allowed to carry out transactions without user identification, while in non-anonymous user identification is mandatory.
It is also necessary to distinguish between electronic fiat money (equal to state currencies) and electronic non-fiat money (not equal to state currencies).
- Link your mobile phone to your account. This is the most convenient and fastest way to restore access to your account. The linked phone will help if you forget your payment password or access the site from an unfamiliar device;
- Use one-time passwords. After switching to enhanced authorization, you will no longer be in danger of theft or interception of your payment password;
- Choose a complex password. It will not be easy for criminals to guess a complex password. Strong passwords are passwords that are at least 8 characters long and include uppercase and lowercase letters, numbers, and multiple symbols such as the dollar sign, pound sign, exclamation point, and so on. For example, $tR0ng!;;
- Do not enter your personal data on sites you do not trust.
Email
Electronic mail is a technology and the services it provides for sending and receiving electronic messages that are distributed in computer network. Typically, an e-mail box looks like this: user_name@domain_name. Also, in addition to transferring plain text, it is possible to transfer files.
- You need to choose the right postal service. There is a huge selection of free email services on the Internet, but it is better to trust those you know and who are the first in the ranking;
- Do not include personal information in personal mail. For example, it's better to select "music_fan@" or "rock2013" instead of "theme13";
- Use two-step authorization. This is when, in addition to the password, you need to enter a code sent via SMS;
- Choose a complex password. Each mailbox must have its own strong, hack-resistant password;
- If there is an opportunity to write your own personal question, use this opportunity;
- Use multiple mailboxes. The first one is for private correspondence with recipients you trust. This email address should not be used when registering on forums and websites;
- After finishing work on the mail service, before closing the tab with the site, do not forget to click on "Exit".
Cyberbullying or virtual bullying
Cyberbullying - harassment with messages containing insults, aggression, intimidation; hooliganism; social boycott through various Internet services.
- Don't jump into the fight. The best way: consult how to behave and, if there is no one to whom you can turn, then first calm down. If you begin to respond with insults for insults, you will only ignite the conflict even more;
- Manage your cyber reputation;
- Anonymity in the network imaginary. There are ways to find out who is behind an anonymous account;
- You should not lead a hooligan image of a virtual life. The Internet captures all your actions and saves them. It will be extremely difficult to remove them;
- Respect your virtual honor from a young age;
- Ignore a single negative. One-time offensive messages are best ignored. Usually aggression stops at the initial stage;
- Ban the aggressor. In instant messaging programs, social networks have the ability to block sending messages from certain addresses;
- If you are a witness to cyberbullying. Your actions: to speak out against the stalker, show him that his actions are evaluated negatively, support the victim who needs psychological help, inform adults about the fact of aggressive behavior on the network.
Mobile phone
Modern smartphones and tablets contain quite adult functionality, and now they can compete with desktop computers. However, there are still very few means of protection for such devices. Testing and searching for vulnerabilities in them is not as intensive as for PCs, the same applies to mobile applications. Modern mobile browsers have almost caught up with their desktop counterparts, but the expansion of functionality entails more complexity and less security. Not all manufacturers release updates that cover critical vulnerabilities for their devices.
- Nothing is truly free. Be careful, because when you are offered free content, it may contain some paid services;
- Think before you send SMS, photo or video. Do you know exactly where they will end up?
- You need to update the operating system of your smartphone;
- Use anti-virus programs for mobile phones;
- Do not download applications from an unknown source, as they may contain malicious software;
- After you leave the site where you entered personal information, go to your browser settings and delete cookies;
- Periodically check which paid services are activated on your number;
- Give me your number mobile phone only people you know and trust;
- Bluetooth must be turned off when you are not using it. Don't forget to check it sometimes.
Online games
Modern online games are colorful, exciting entertainment that unites hundreds of thousands of people around the world. Players explore the world given to them, communicate with each other, complete tasks, fight monsters and gain experience. They pay for pleasure: they buy a disc, pay for a subscription, or purchase some options.
All these funds are spent on maintaining and developing the game, as well as on security itself: authorization systems are being improved, new patches are being released (digital patches for programs), server vulnerabilities are being closed. In such games, it is not so much your rivals that you should be afraid of, but the theft of your password, on which the authorization system of most games is based.
- If another player behaves badly or creates trouble for you, block him in the list of players;
- Complain to the game administrators about the bad behavior of this player, it is advisable to attach some evidence in the form of screenshots;
- Do not provide personal information in the game profile;
- Respect other participants in the game;
- Do not install unofficial patches and mods;
- Use complex and different passwords;
- Even during the game, do not turn off the antivirus. While you are playing, your computer may be infected.
Phishing or identity theft
The usual theft of money and documents today is no surprise to anyone, but with the development of Internet technologies, attackers have moved to the Internet and continue to do their “favorite” business. So there was new threat: Internet fraud or phishing, the main objective which consists in obtaining confidential user data - logins and passwords. In English, phishing reads like phishing (from fishing - fishing, password - password).
- Follow your account. If you suspect that your profile has been hacked, then you need to block it and inform the resource administrators about it as soon as possible;
- Use secure websites, including online stores and search engines;
- Use complex and different passwords. Thus, if you are hacked, then the attackers will have access to only one of your profiles on the network, and not to all;
- If you have been hacked, then you need to warn all your friends who are added to your friends that you have been hacked and, possibly, spam and links to phishing sites will be sent on your behalf;
- Set a strong password (PIN) on your mobile phone;
- Disable password saving in the browser;
- Do not open files and other attachments in emails, even if they come from your friends. Better ask them if they sent you these files;
Digital Reputation
Digital reputation is negative or positive online information about you. Compromising information posted on the Internet can seriously affect your real life. "Digital reputation" is your image, which is formed from information about you on the Internet. Your place of residence, study, yours financial position, character traits and stories about loved ones - all this accumulates in the network.
Many teens are reckless about posting personal information online, not understanding the potential repercussions. You will not even be able to guess that a photo posted 5 years ago was the reason for not hiring you.
REMINDER FOR CHILDREN AND TEENAGERS
SAFETY RULES FOR STUDENTS ON THE INTERNET
1. Norms of behavior and moral principles are the same both in the virtual and in the real world.
2. Illegal copying of the products of other people's work (music, games, programs, etc.) is considered plagiarism (intentional appropriation of the authorship of someone else's work).
3. Don't believe everything you see or read on the internet. If you have any doubts about the veracity of any information, you should seek the advice of an adult.
4. Do not share your personal information with other Internet users (address, phone number, school number, favorite places to play, etc.).
5. If you chat, use instant messaging programs, play network games, are doing something online that requires a user ID, then choose that username with adults to make sure it doesn't contain any personal information.
6. Internet friends may not really be who they say they are, so you should not meet Internet friends in person.
7. You can't open files sent by people you don't know. These files may contain viruses or photos/videos with objectionable content.
8. Learn to trust your intuition. If anything on the Internet makes you feel psychologically uncomfortable, share your impressions with adults.
Basic rules for elementary school students
You should know
1. Always ask your parents about unfamiliar things on the Internet. They will tell you what is safe to do and what is not.
2. Before you start making friends online, ask your parents how to communicate safely.
3. Never tell strangers about yourself. Where you live, what school you go to, only your friends and family should know the phone number.
4. Don't send photos to people you don't know. Don't let strangers see your private photos.
5. Do not meet without parents with people from the Internet live. On the Internet, many people tell lies about themselves.
6. When communicating on the Internet, be friendly with others. Do not write rude words, reading rude words is as unpleasant as hearing them. You may inadvertently offend someone.
7. If someone upset or offended you, be sure to tell your parents.
Basic rules for middle school students
You should know
1. When registering on the sites, try not to provide personal information, because. it may be accessible to strangers. It is also not recommended to post your photo, thereby giving an idea of how you look to strangers.
2. Only use the webcam when chatting with friends. Make sure that strangers do not have the opportunity to see you during a conversation, because. it can be recorded.
3. Unwanted emails from strangers are called spam. If you receive such a letter, do not reply to it. If you reply to such an email, the sender will know that you are using your email address. mailbox and will continue to send you spam.
4. If you received a message from an unknown address, it is better not to open it. Such emails may contain viruses.
5. If you receive letters with unpleasant and offensive content, if someone behaves inappropriately towards you, report it.
6. If someone upsets or offends you, tell an adult.
Basic rules for high school students
You should know
1. It is undesirable to place personal information on the Internet.
2. Personal information is your mobile phone number, address Email, home address and personal photos.
3. If you publish photos or videos on the Internet, everyone can see them.
4. Do not respond to spam (unsolicited email).
5. Don't open files sent by people you don't know. You cannot know what these files actually contain - they may contain viruses or photos/videos with "aggressive" content.
6. Do not add strangers to your IM contact list (ICQ, MSN messenger, etc.)
7. Remember that virtual acquaintances may not be who they say they are.



Since people exist in society, they are all obliged to comply with the norms of social behavior. Etiquette rules can be of a general nature, and also vary depending on the communicative situation, therefore, they distinguish, for example, table etiquette, business etiquette, diplomatic etiquette, etc. AT last years added to this list the new kind- network etiquette, or netiket. His appearance was dictated by an urgent need. After all, Internet users today are a huge number of people, and not all of them have an idea of how to behave correctly when communicating online.
Why do we need netiquette rules?
The rules of online etiquette, in fact, have the same purpose as the usual etiquette prescriptions: they help people reach mutual understanding, and ensure the safety of communication. The impersonality of the network communicative act makes users forget that they are still dealing not with a machine, but with living people. It is rather difficult to establish a strong contact with an interlocutor whom we do not see or hear. And Netiquet is a set of recommendations that are designed to help in solving this problem. In addition, following the rules of network etiquette makes it possible to safely avoid the intrigues of virtual scammers, keeping your wallet and your nerve cells intact.
10 basic netiquette rules
- Be polite, even if the communication is not in real time. After all, in any case, you are in contact with people who are simply on the other side of the screen.
- Do not forget about the obligatory formulas of greetings, farewells, addresses, expressions of gratitude, etc.
- Pay attention to the communication situation, for example, in an online chat where people are just going to chat, you can behave more freely, but during an online topical conference, you should be more restrained, etc.
- Avoid idle talk, and try not to waste the interlocutor's time in vain.
- Do not rush to destroy the aura of anonymity in a situation of communicating with strangers, let people judge you not by your appearance and manner of dressing, but by the breadth of your horizons, literacy level, sense of humor, etc.
- Proofread and edit your messages and emails before sending, do not send nonsense or illiterate text to the interlocutor.
- Don't stoop to harsh insults. Politeness is appropriate even when your opponent turns out to be an outright boor.
- Do not refuse help, unless, of course, you are asked to send money to an unknown number or something like that. You can help with advice, send a link to the right resource, answer a question, give advice.
- Do not try to teach the interlocutor or morally “pressure” him.
- Be condescending to the mistakes of others, it is quite possible to close your eyes to involuntary flaws in phrases. No one is perfect, we are all only human.
Rules of social media etiquette

Social networks are incredibly popular today, and therefore they could not help touching network etiquette and the basic rules of communication in social networks are generally similar to the instructions of a general netbook. But there are also special recommendations. For example, in order to avoid confusion, it is best to use a simple name as a nickname or your real first and last name, as well as your profile photo. But to report information about yourself of a purely personal nature - phone number, address, passport details, etc. - Interlocutors on the network should not be, so that there is no risk of deception by scammers. You should not continue to communicate with a user who seems suspicious or inadequate to you. It can be blacklisted or reported to administrators.
The concept of network etiquette came to us from English - network etiquette. Often there they shorten the expression to netiquette. In Runet, the term "setiket" is not yet widespread. To make online communication pleasant and negotiations successful, some principles should be taken into account, just like in real life. Network etiquette is a set of rules for online communication, correspondence, mailings, exchange of opinions, knowledge, experience, and so on.
About the rules
The rules of network etiquette are not much different from the rules in real life. Be polite, listen carefully (read) to the interlocutor, respect his opinion, do not slander, do not be rude.
Speak clearly, concisely and to the point. Do not get into skirmishes, do not use mate, try not to make mistakes in the texts of messages.
But virtual communication has its own characteristics, so there are some special points and terms. Let's consider each in more detail.
offtopic
This term means any message that goes beyond the designated topic. That is, if in some branch there is a discussion of injection engines, there is no need to try to express your opinion there about the last football match and the dress from the new collection.
Offtopics are not approved by moderators, and you may be banned from leaving messages (ban, ban). In some topics, unacceptable statements (offtopics) are immediately clearly specified in order to predict the development of the discussion and not let it go beyond the necessary framework.

flood
Network communication etiquette prescribes not to spread the flood for the good reputation of the user on the Internet. After all, no one likes noise, and "flooders" just make noise, leaving a lot of meaningless comments like "Cool!", "Tin!", "High!", trying to attract attention to themselves. Mark what you really find interesting. Let it be a meaningful phrase expressing your opinion, and not "Chic!". Otherwise, you are guaranteed a ban.
Emoticons
These are funny images for additional emotional coloring of the text, which are now very much on the net. Every decent site or forum provides users with their own set of emoticons, static or animated. Despite their popularity, they must be used with great care. One or two images per message is enough. A large number of make the text hard to read or even deprive it of semantic load.

Trolling
This term also came to us from of English language, where he means catching fish with a lure.
In network communication, trolling is the writing of rude, contradictory, provocative messages in order to quarrel, insult, and anger the participants in the discussion.
A person who leaves such remarks, a troll, most often acts covertly and solely for his own pleasure. It is not the result that is important to him, but the process - the correspondence itself, the reaction of people to his statements.
Moderators are fighting this phenomenon with all their might, because a confident and active troll can scare away visitors.
The basic rule of network etiquette is politeness. Try to adhere to it always, even if you find yourself in an unpleasant situation (conversation), get out of it first, do not succumb to provocations. Don't let them troll you.

Literacy and abbreviations
Try to write correctly. Check your text carefully. Now there are enough programs and resources to help you online - a courtesy in real life. Yes, there are already enough words on the Internet that are misspelled, but are perceived as correctly spelled - this is a kind of network slang, but they should not be abused.
In addition to slang words, network etiquette also allows:
- IMHO - my humble opinion.
- LOL - my loud laugh.
- BTW - by the way.
- AFAIK - as far as I know.
- WBR - my best wishes.
- AKA - known as.
- WTF is a swear word.

netiquette: email
Correspondence, especially business, is a separate block in the list of communication rules on the network. How to compose a competent, pleasant letter for the interlocutor, which he is likely to read and then will have a desire to answer it? Moreover, write in such a way that his answer meets your expectations?
- First, introduce yourself. Abstract, general contact information is enough for pleasant communication. Indicate your real name, and the correspondence will work out. Users are very wary of anonymous emails, often sending them to spam without even reading them.
- Secondly, specify the subject of the letter. It should reflect the content of the message, be bright, capacious, concise, arouse interest and desire to read the letter. For example, "Do you dream of having a rest? Waiting for you, and even better individually -" Sergey Vasilievich, a vacation especially for you!
- Third, think carefully about the content. Check the text for errors. Keep it short and to the point, don't spill water. If the message is long, it may not be read. Divide the message into semantic paragraphs, key points can be highlighted in capital letters, but no more than two or three words.
- Fourth, the design should be delicate. Most messaging programs support a lot of fonts, colors, pictures, but this does not mean that everything must be used. For an interlocutor, such a bright letter can cause irritation or even be displayed incorrectly. Pairs or colors are enough.
- Fifth, be moderate in quoting. When there is an active correspondence, network etiquette advises not to erase all previous messages when answering, but also not to forward the entire branch. The best option- leave the original text and a few of the following, so that the main meaning of the conversation is clear.
- Sixth, a concise signature. The rules of network etiquette say that the optimal signature size is four lines. Usually they write the name and contact information. Do not confuse signature and business card, you do not need to insert pictures, tables and diagrams here. From the signature, the reader should find out who wrote to him and how this person (you), if desired, can be contacted.

Newsletters
What is network etiquette? Network communication rules. What are distributions? Mass communication. So, even if you send a message to many and possibly complete strangers, you will have to follow some rules.
If you don't care if the people you send emails need your information, that's spam. The concept is very negative in the network. For some time now even pursued by the law. It is better to gather an official circle of subscribers to be sure that your letter will not be thrown into spam, that they are waiting for it.
When composing a letter for a certain circle of people, always fill in the subject of the letter, the mailing should be thematic.
Write additional addresses in the "blind copy" (BCC) subject. It is not very pleasant for any person to be one of tens, hundreds, thousands ... Individual attention is pleasant to him. You also do not need to show the addresses of your subscribers.
Do not reply to spam emails yourself. If they annoy you, put a filter or contact your ISP for help.
If you are forwarding information, copy the text directly and paste it into a new letter. Avoid multiplying ">" signs that automatically appear when forwarding and make the text unreadable.
Do not send heavy files and archives to your interlocutors without asking permission. Many have restrictions on the weight of incoming letters, and then your message will not reach the addressee, the correspondence may be interrupted. Unsolicited archives also arouse suspicion and rejection. Especially if they are self-extracting (.exe).
For personal comfort, set the filter to and do not unpack archives from strangers, they may contain viruses.

Network etiquette
Communicating online, you create your image. Interlocutors know you exclusively by your own virtual statements and actions. But behind any car there is a person who, perhaps, will be a good acquaintance to you, a good friend in real life. Do not neglect the rules of network etiquette. Be polite, do not splash out negative emotions on the audience.
Try to write correctly yourself, but do not pay attention, especially do not point out mistakes to others. If there are a lot of them and they are repeated regularly, write a personal letter to the person with wishes and advice, but do not insist and do not ridicule - we all make mistakes sometimes.
Very delicately introduce humor, irony, sarcasm into your messages. They may not be accepted or offend the interlocutor. In developing correspondence, start with very popular or already established phrases and expressions in order to understand the level of perception of the interlocutor.
Don't be arrogant. Even if you are a great specialist in some area, give polite and detailed answers to beginners, explain the terms and principles, because you yourself once started.







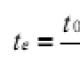


For beginners: breeding a broiler at home Boiled water for broilers
Only lovers will survive
Features of advertising aimed at children
retouching old photos in photoshop retouching old photos
What is an NPO: decoding, definition of goals, types of activities Does a non-profit organization have the right