Although we have seen a powerful explosion of interest in the Internet of Things in the last few years, the concept of technology has existed since 1999, and even then the scale of its nature was felt. Indeed, the aggregation of data from connected devices and sensors helps both optimize business processes and provide more personalized and high-quality services/infrastructure to the consumer.
It is important to realize that the effective development of IoT should come down not only to the penetration of "connected" devices into all aspects of life, but to the creation of a technological ecosystem, in other words, to the integration of solutions for collecting, transmitting, aggregating data on a platform that allows you to process data and use it. to implement effective solutions.
The Internet of Things hides enormous potential, but it will only be revealed through the interaction of separate networks deployed to solve individual problems.
Although historically IoT solutions were used mainly as elements of disparate systems, more and more complex solutions are now appearing on the market. And this is not surprising: according to IDC, the total global investment in solutions based on the Internet of Things was $737 billion in 2016, more than $800 billion in 2017, and by 2021 investments will grow to approximately $1.4 trillion.
Technological trends at the heart of the Internet of things
For wireless transmission data, and, therefore, the effectiveness of the implementation of the Internet of things, such factors as productivity at low speeds, fault tolerance, and adaptability are paramount. Here, the catalysts were primarily the high level and standard of NB-IoT for building the Internet of things, adopted by the world community, whose development and distribution led to an increase in the number and decrease in the cost of IoT devices.

In 2019, PWC experts determined that, in general, the development of IoT has become real thanks to technological trends driven by both the state and business:
- a rapid increase in the number of sensors and connected devices;
- reduction in the cost of data transmission, which made it possible to redirect investments into large processing systems;
- the development of cloud technologies and which provide a flexible system for storing and analyzing data in the face of a constant increase in the amount of data;
- reduction in the cost of computing power: processors, memory and storage systems.
Implementation of IoT at the state level
Various public-private partnerships are now popular, related, for example, to energy service solutions for smart meters for housing and communal services, security systems, an intelligent transport system - in other words, with all manifestations of Smart City.
For example, in the power industry, the Internet of Things can bring significant change by digitalizing the traditional electromechanical system. This approach is especially relevant for Russia, which has a historically established large-scale centralized power supply system that connects more than 2.5 million kilometers of power lines, about 500,000 substations, and 700 power plants with a capacity of more than 5 MW.
Although today the penetration of IoT technology into the Russian energy industry is only at the very beginning, we already have successful examples its implementation.
For example, the Moscow United Energy Company, together with MTS, has been implementing a project for monitoring energy consumption at 23,000 facilities since 2019, while T Plus, Mosenergo and Tatenergo are actively implementing equipment condition forecasting systems.
Or let's take housing and communal services, which would seem to be a rather conservative sphere. However, here smart sensors successfully solve the main tasks - monitor resource consumption and prevent emergencies, and allow you to take readings at any time.
A unified integrated GIS system for housing and communal services has been operating in our market, launched in all regions of Russia since 2016, while since the beginning of 2018 all data collection organizations are legally required to transfer information to it. Therefore, citizens can monitor energy consumption information in real time and adjust consumption.

The IoT segment is also growing rapidly in the healthcare sector, especially in terms of online health monitoring, rehabilitation assistance, and tracking the safety of medicines. Now that wearable sensors that are compact and do not require recharging for many months are able to measure activity, duration and quality of sleep, breathing, pressure, pulse, real-time tracking of physical condition will become the foundation for high-quality treatment and maintenance programs, and by 2020 will lead to an increase in the total market value of intelligent health care to $169.3 billion.
According to analysts at Vodafone, the integration of technologies such as cloud services and IoT will make the healthcare industry more efficient and save up to $290 billion. in the medium term only due to the fact that the recommendations of doctors will be followed by patients much more carefully.
Smart solutions, automation and robotization of processes are gradually changing the niche of transport and logistics in general. And no wonder: in a sphere where the length various kinds transport routes exceeds 1.6 million kilometers, and the number of trucks is already 7 million units, it is simply impossible to do without remote monitoring systems.
Tracking road congestion, monitoring the movement and safety of goods, optimizing navigation operations, preventing wear of parts ... Quite a few manufacturers of remote vehicle monitoring devices (Omnicom, GALILEO, Naviset, Mercury, M2M Cyber) are already developing on the domestic market, and a whole package is also being developed software products, allowing you to analyze the received data and optimize costs and processes.
The achievements of each individual area, made possible by the integration of the Internet of things, can be considered endlessly, but it is the integrated IoT solutions that will give citizens a truly smart city, in which everything will be optimized: from video surveillance and transport management to monitoring the environment and healthcare.
Business driven IoT adoption
Digitalization process large enterprises that have been operating since Soviet times, in most cases does not go easily: you need to bring the entire IT infrastructure, strategy and resource costs to the same denominator. And here it is IoT that allows you to get all the information you need for this, reduce costs and develop new sources of income, that is, get competitive advantage. For example, reduce system latency or improve system performance.
In addition to using smart sensors to optimize their own operations, businesses are flooding the consumer market with IoT devices, which MarketsandMarkets analysts predict will grow to $104.4 billion by 2023.
This growth is due to the fact that due to the high degree of penetration of services mobile communications and fixed broadband access Internet, a huge number of consumer devices have appeared with the ability to connect to the network and remotely control them.
With the development of such technologies, humanity has received a new quality of life, got rid of doubts in the spirit of “it seems that I didn’t close / didn’t turn off something”, unnecessary expenses, unpleasant situations like suddenly running out of fuel in a car and food in the refrigerator - now your concern is daily comfort can be entrusted to technological progress.
In general, among the whole variety of consumer devices with access to the Internet, J'son & Partners analysts identified four groups designed to optimally solve everyday tasks:
- control of IoT devices (smartphones, tablets, Smart TVs and so on),
- smart home (smart resource management systems, security systems, smart home appliances, etc.),
- high-tech wearable devices (medical devices, fitness gadgets, network-connected wearable cameras),
- consumer devices for a personal car (sensors for insurance telematics, transponders for contactless fare payment).
How to secure the Internet of Things
To date regulation The use of Internet of Things technologies is reduced to compliance with minimum security requirements. In Russia, the strongest legal restrictions related to industrial automation (the law on critical infrastructure, the order of the FSTEC, GosSOPKA FSB), provoked by frequent attacks on industrial IoT.
IoT consumer devices are not yet of great interest to attackers and, as a result, protection in this area is not strong enough.

In general, IoT security consists of four components.
- Remote communication security. The communication channel must be secured with encryption, two-factor authentication, and authentication so that devices know who can be trusted and who is a scammer.
- Device protection. In addition to the initial integrity and reliability of the program code, it is important to ensure the security of connected devices in the future, that is, connection control, intrusion protection, potential threat analysis, and so on.
- Operation control. You should monitor the device even after a long time has passed since its launch: update the software in a timely manner, control threats and take them into account in new firmware.
- Network interaction control. Analytics systems will help to avoid threats, as they will make it possible to study the behavior of the consumer on the network and in time to track anomalies or suspicious activity.
From these "bricks" it is possible to build a reliable security system that can prevent or at least mitigate threats to the Internet of things, whether it be unforeseen loads or targeted attacks.
Prospects for the development of the Internet of things in Russia
Russian trends in the field of IoT mainly reflect international trends, but only with some delay. Although the Internet of Things in the domestic market has already penetrated almost all industries, at the moment the consumer segment of the IoT market (delivery of goods and food, carsharing, smart devices) is the most developed in our country.
J "son & Partners Consulting analysts have calculated that by 2022 the volume Russian market Internet of Things will amount to about 90 billion rubles (with an average annual growth rate of 12.5%). But IDC has identified the main factors affecting the development of the IoT market in Russia:
- the formation of strategic initiatives by the state to build digital enterprises,
- optimization of business processes,
- integration information technologies with the operating activities of companies,
- increased competition within industries.
Needless to say, the Internet of Things has become an important part of everyday reality. With its help, the interaction of objects, systems and people is really getting better, because it is IoT devices that become Starting point to implement many other technologies, such as AI or ML, that allow you to analyze data deeper and use it to improve the quality of life and create a smart ecosystem that is more and more comfortable for people.
AWS IoT Device Defender is a fully managed service that helps you secure your fleet of IoT devices. AWS IoT Device Defender continuously audits your IoT configurations to make sure that they aren't deviating from security best practices. A configuration is a set of technical controls you set to help keep information secure when devices are communicating with each other and the cloud. AWS IoT Device Defender makes it easy to maintain and enforce IoT configurations, such as ensuring device identity, authenticating and authorizing devices, and encrypting device data. AWS IoT Device Defender continuously audits the IoT configurations on your devices against a set of predefined security best practices. AWS IoT Device Defender sends an alert if there are any gaps in your IoT configuration that might create a security risk, such as identity certificates being shared across multiple devices or a device with a revoked identity certificate trying to connect to AWS IoT Core .
AWS IoT Device Defender also lets you continuously monitor security metrics from devices and AWS IoT Core for deviations from what you have defined as appropriate behavior for each device. If something doesn't look right, AWS IoT Device Defender sends out an alert so you can take action to remediate the issue. For example, traffic spikes in outbound traffic might indicate that a device is participating in a DDoS attack. AWS IoT Greengrass and Amazon FreeRTOS automatically integrate with AWS IoT Device Defender to provide security metrics from the devices for evaluation.
AWS IoT Device Defender can send alerts to the AWS IoT Console, Amazon CloudWatch, and Amazon SNS. If you determine that you need to take an action based on an alert, you can use AWS IoT Device Management to take mitigating actions such as pushing security fixes.
Keeping Connected Devices Secure
Why is IoT security important?
Connected devices are constantly communicating with each other and the cloud using different kinds of wireless communication protocols. While communication creates responsive IoT applications, it can also expose IoT security vulnerabilities and open up channels for malicious actors or accidental data leaks. To protect users, devices, and companies, IoT devices must be secured and protected. The foundation of IoT security exists within the control, management, and set up of connections between devices. Proper protection helps keep data private, restricts access to devices and cloud resources, offers secure ways to connect to the cloud, and audits device usage. An IoT security strategy reduces vulnerabilities using policies like device identity management, encryption, and access control.
What are the challenges with IoT security
A security vulnerability is a weakness which can be exploited to compromise the integrity or availability of your IoT application. IoT devices by nature, are vulnerable. IoT fleets consist of devices that have diverse capabilities, are long-lived, and are geographically distributed. These characteristics, coupled with the growing number of devices, raise questions about how to address security risks posed by IoT devices. To further amplify security risks, many devices have a low-level of compute, memory, and storage capabilities, which limits opportunities for implementing security on devices. Even if you have implemented best practices for security, new attack vectors are constantly emerging. To detect and mitigate vulnerabilities, organizations should consistently audit device settings and health.
AWS IoT Device Defender helps you manage IoT security
Audit device configurations for security vulnerabilities
AWS IoT Device Defender audits IoT configurations associated with your devices against a set of defined IoT security best practices so you know exactly where you have security gaps. You can run audits on a continuous or ad-hoc basis. AWS IoT Device Defender comes with security best practices that you can select and run as part of the audit. For example, you can create an audit to check for identity certificates that are inactive, revoked, expiring, or pending transfer in less than 7 days. Audits make it possible for you to receive alerts as your IoT configuration is updated.
Continuously monitor device behavior to identify anomalies
AWS IoT Device Defender detects anomalies in device behavior that may indicate a compromised device by monitoring high-value security metrics from the cloud and AWS IoT Core and comparing them against expected device behavior that you define. For example, AWS IoT Device Defender lets you define how many ports are open on the device, who the device can talk to, where it is connecting from, and how much data it sends or receives. Then it monitors the device traffic and alerts you if something looks wrong, like traffic from devices to a known malicious IP or unauthorized endpoints.
Receive alerts and take action
AWS IoT Device Defender publishes security alerts to the AWS IoT Console, Amazon CloudWatch, and Amazon SNS when an audit fails or when behavior anomalies are detected so you can investigate and determine the root cause. For example, AWS IoT Device Defender can alert you when device identities are accessing sensitive APIs. AWS IoT Device Defender also recommends actions you can take to minimize the impact of security issues such as revoking permissions, rebooting a device, resetting factory defaults, or pushing security fixes to any of your connected devices.
How does AWS IoT Device Defender work
AWS IoT Core provides the security building blocks for you to securely connect devices to the cloud and to other devices. The building blocks allow enforcing security controls such as authentication, authorization, audit logging and end-to-end encryption. However, human or systemic errors and authorized actors with bad intentions can introduce configurations with negative security impacts.
AWS IoT Device Defender helps you to continuously audit security configurations for compliance with security best practices and your own organizational security policies. For example, cryptographic algorithms once known to provide secure digital signatures for device certificates can be weakened by advances in the computing and cryptanalysis methods. Continual auditing allows you to push new firmware updates and redefine certificates to ensure your devices stay ahead of malicious actors.
Continuous compliance and adoption of security best practices
The AWS IoT security team is continuously updating a knowledge base of security best practices. AWS IoT Device Defender makes this expertise available in a service and simplifies the process of establishing and auditing best practices within your AWS IoT environment. AWS IoT Device Defender helps you mitigate the risk of introducing security issues during the development and deployment of your IoT application by automating the security assessment of your cloud configurations and device fleets so you can proactively manage security issues before they impact production.
Attack surface evaluation
With AWS IoT Device Defender, you can identify attack vectors applicable to your specific IoT devices. Having this visibility allows you to prioritize eliminating or hardening the relevant system components based on the operational requirements. For example, you can configure AWS IoT Device Defender to detect use of insecure network services and protocols with known security weaknesses. Upon detection, you can plan the appropriate remediation to prevent unauthorized device access or possible data disclosure.
Threat impact analysis
AWS IoT Device Defender can facilitate impact analysis of publicly or privately disclosed attack campaigns on your IoT devices. You can define detection rules in AWS IoT Device Defender based on known indicators of compromise to identify vulnerable devices or devices already compromised. For example, the detection rules can monitor IoT devices for indicators such as network connections to known malicious command and control servers and backdoor service ports open on devices.
Customers

In accordance with the multi-level, the following 3 areas can be distinguished where it is necessary to ensure information security:
- smart-devices- "smart" sensors, sensors and other devices that collect information from equipment and send it to the cloud, transmitting control signals back to change the state of things;
- network gateways and data channels(wired and wireless protocols);
- softwareIoT-platforms- cloud storage and information processing services.
For all these components in particular and in general for the IoT system, the following cybersecurity measures are relevant:
- organizational arrangements
- creation and implementation common policy information security of the enterprise, taking into account all applications and systems Industrial;
- development of rules for the safe use of IoT devices and networks;
- improvement of legislative provision of privacy and industrial secrets;
- public and private standardization and certification of devices, data transmission channels, information storages and application software for processing and analysis;
- technical tools protection of data from leaks, loss and interception of control:
- encryption and other cryptographic methods, incl. personalization of IoT devices using unique IDs, MAC addresses, keys and certificates that provide a sufficiently high level of cybersecurity at no additional cost ;
- flexible access control policies with multi-factor authorizations;
- redundancy, replication, organization of a secure perimeter and other information security tools for which we have already considered.
 IoT small data and flows in a cloud IoT platform
IoT small data and flows in a cloud IoT platform Responsibilities of the parties for the cybersecurity of IoT systems
Developers of IoT solutions, including equipment manufacturers, can provide the following cybersecurity measures:
- use modern and reliable software development tools (API, libraries, frameworks, protocols, etc.) and hardware solutions (boards, controllers, etc.);
- reduce the number of components needed to operate the equipment, since each additional element is a potential source of various vulnerabilities, incl. physical breakdowns. For example, you should add USB ports only if they are really needed for the smart device to work.
- implement secure authentication, encrypted session negotiation, and user authentication;
- ensure regular release of software updates to eliminate found and potential vulnerabilities.
However, not only the developers of its software and hardware components are responsible for ensuring the information security of the Internet of Things. Since users of IoT systems are the first to suffer from hacking or data loss, it is they who should take care of protecting their devices and applications. To do this, you need to perform the following fairly simple manipulations:
- do not use logins and passwords pre-installed by the manufacturer as working ones - it is worth creating a new user account with limited access rights;
- set a “complex” password for your home/corporate network and enable network traffic encryption;
- Regularly update smart device software from trusted sources.
 Ensuring information security and data protection in IoT systems is the responsibility of users
Ensuring information security and data protection in IoT systems is the responsibility of users Technical means of ensuring cybersecurityBig Data inIoT-systems
Created and implemented new data transfer protocols In particular, the 6LoWPAN (IPv6 over Low-Power Wireless Personal Area Networks) standard is becoming popular. This networking technology allows efficient transmission of IPv6 packets in small link layer frames (low power wireless networks) as defined in the IEEE 802.15.4 wireless standard. How exactly this protocol and other network technologies with cryptographic means provide secure data transfer in IoT systems, we tell.
 Cryptographic data protection methods are successfully working in the field of
Cryptographic data protection methods are successfully working in the field of Standardization and certificationIoT-systems
Despite the fact that this area of activity is not controlled by an individual user of the IoT system, but is regulated by industry giants or entire states, it is very important for the end client - an enterprise or an individual.
In 2016, the European Commission began preparations for the introduction of mandatory certification of IoT devices. This solution was supported by some manufacturers of popular chips (Infineon, NXP, Qualcomm, STMicroelectronics) used in smart devices. It was proposed to develop and implement basic Internet of Things cybersecurity standards. As part of this initiative, since May 2019, an international standard for the security of the Internet of Things - ISO / IEC 30149 (IoT) - Trustworthiness frameworks has been developed. Domestic 194th technical committee of Rosstandart "Cyber-Physical Systems" received the status of co-editor.
The standard regulates the power of attorney of the information and physical components of IoT systems: reliability, functional security, information security, personal data security, stable operation under attack. The approval of the international standard ISO/IEC 30149 is planned for 2021. In parallel, specialists from the 194th Committee of Rosstandart are also developing a national equivalent of the international standard, which is also planned to be approved in 2021.
However, cybersecurity issues of the Internet of things are of concern not only to government officials. Private companies, as well as independent expert communities, are also involved in the certification of IoT systems. For example, the Online Trust Alliance has released the IoT Trust Framework, a set of criteria for developers, device manufacturers, and service providers that aims to improve the security, privacy, and lifecycle of their IoT products. This document is primarily focused on consumer, office and wearable IoT devices and is the basis for several certification and risk assessment programs. [ 4 ] .
In 2018, ICSA Labs, an independent division of Verizon, launched the IoT security testing and certification program. It tests and evaluates the following components of IoT systems: notification/logging, cryptography, authentication, communication, physical security, and platform security. Devices that pass certification will be marked with a special ICSA Labs seal of approval, which indicates that they have been tested and the vulnerabilities found have been fixed. Also, certified devices will be observed and periodically tested throughout their life cycle to ensure their safety. [ 4 ] .
A similar program for testing and certification of IoT products was launched by UL Cybersecurity Assurance (). Certification certifies that the solution provides a reasonable level of protection against risks that could lead to inadvertent or unauthorized access, modification, or failure. Also certifies that updates or new versions of the software for the certified product or system will not reduce the level of protection that exists at the time of evaluation. IoT security experts believe that the greatest benefit from such certification programs will be achieved if not a single smart device is tested, but the entire ecosystem, infrastructure, data transmission channels, applications, etc. [ 4 ] .
However, even the availability of certificates confirming the compliance of the IoT system with the requirements of private programs, public initiatives or international standards information security does not guarantee 100% protection of the Internet of things. It is also worth noting some Negative consequences activities to increase the level of protection of the Internet of things from hacking and data loss [ 6 ] :
- multi-factor authentication systems introduce additional and often inconvenient actions for users, which annoys them;
- complex cryptographic operations and the need for secure data storage significantly increase the cost of microcircuits;
- work to ensure cybersecurity significantly increases the time and cost of creating each component of the IoT system.
 Making it safe is a complex task that everyone needs, from the state to the end user
Making it safe is a complex task that everyone needs, from the state to the end user About methods and means of network security of the Internet of Things read in ours, and master modern tools for protecting big data in our practical courses in a specialized training center for managers, analysts, architects, engineers and researchers in Moscow:
| DSEC: | HADM: |
 |
|
 |
Sources
, , ,Post navigation
New on site
Reviews on Google
Studied on the Hadoop Administration course. The course was led by Nikolay Komissarenko. Well-prepared, well-thought-out, systematic course program. Workshops organized so that students have the opportunity to get acquainted with the real features of the product under study. I turned off my head and clicked the labs on the book - it doesn’t work here. The teacher easily and in detail answers the questions that arise not only on the topic of the subject, but also on related ones. read more
Completed Apache Kafka administration course. I liked both the presentation of the material and the structure of the course. Only now it turned out that there was not enough time ... I didn’t manage to do everything finish, but it's not up to the course of the claim :). There was quite a lot of practice, and it's good read more
Completed the "Hadoop for Data Engineers" course taught by Nikolay Komissarenko. The information is very relevant and useful, makes you think about current methods work with large data in our company and possibly change something. Classes with a lot of practice, so the material is well absorbed. Special thanks to Nikolai for explaining some things in a simple language, understandable even for "dummies" in the Hadoop area. read more
There are more and more devices connected to the Internet of Things. Global business is on the verge of universal digitalization, which makes it more vulnerable to modern security threats. Take advantage the latest technologies to assess the vulnerability and risks to the company. Research and select a strategy to mitigate the risks associated with security threats to IoT systems.
The world needs more experienced cybersecurity professionals. Familiarity with IoT security systems will be an advantage. Take the course and become an IoT Network Security Specialist in addition to your existing CCENT/CCNA Routing & Switching and CCNA Security certifications. If you already have a CCNA Cybersecurity Operations certification, this course will make you more in-demand in the job market. You will know how attacks work and how to neutralize them.
2020: Great Britain prepares the law on protection of IoT devices
On January 28, 2020, it became known that the UK Government unveiled a bill aimed at protecting IoT devices.
The bill contains three main requirements for manufacturers of "smart" devices. In particular, all passwords of user IoT devices must be unique and without the ability to reset them to "universal" factory settings; manufacturers must provide a public point of contact so that everyone can report a vulnerability and count on “timely action”; Manufacturers must clearly state the minimum time period during which devices will receive security updates at the point of sale.
The regulation was developed by the UK Department for Culture, Media and Sports after a lengthy period of consultation that began in May 2019.
According to the UK government, the bill is planned to pass "as soon as possible".
Theoretical Aspects of Information Security of the Internet of Things
There is no secure IoT ecosystem
Experts insist that IoT market service and device providers violate the end-to-end information security (IS) principle, which is recommended for all ICT products and services. According to this principle, information security should be laid down at the initial stage of designing a product or service and maintained until the end of their life cycle.
But what do we have in practice? Here, for example, is some data from the corporation's research (summer 2014), the purpose of which was not to identify any specific unsafe Internet devices and convict their manufacturers, but to identify the problem of information security risks in the IoT world as a whole.

Ransom for entry home?
Alternatively, the installation of special unified chips on network devices that will protect them from hacker attacks is not excluded. These measures, according to officials of the European Commission, should increase the level of trust in the Internet of things in society and prevent hackers from creating botnets from connected equipment.

| Measures to protect the Internet of things from hackers should be taken at the state level, since not only the devices themselves need to be controlled, but also the networks to which they are connected, as well as cloud storage. The IoT certification scheme is comparable to the European labeling system for energy products adopted in 1992. Marking is mandatory for cars, household appliances and electric lamps. But manufacturers of equipment consider the system of such marking to be ineffective in protecting against hackers. Instead, they would prefer to install a standard chip in the devices, which will be responsible for the security of the Internet connection.
|
The group of devices connected to the Internet includes video cameras, televisions, printers, refrigerators and other equipment. Most of these devices are not adequately protected from hacker attacks. By themselves, these devices may not be of interest to criminals. However, hackers hack them to use them as robots to create botnets, through which more serious systems can be attacked. Most owners of hacked devices are not even aware of how their technology is being used.
As an example, a large-scale DDoS attack on the Krebs On Security Internet resource in September 2016 is given.
| The intensity of requests from the botnet during the attack reached 700 Gb/s. The botnet includes more than 1 million cameras, video recorders and other devices connected to the Internet of things. This is not the first high-profile case when such devices become part of a botnet, but for the first time the network consisted almost entirely of such devices.
|
Market assessment
2017: Expenses on security of IoT in $1.2 billion
On March 21, 2018 the analytical company Gartner published results of a research of the world market of information security in the field [[Internet of Things Internet of Things (IoT)|[[Internet of Things Internet of Things (IoT)|[[Internet of Things Internet of Things (IoT)|[ [Internet of Things Internet of Things (IoT)|[[Internet of Things Internet of Things (IoT)|[[Internet of Things Internet of Things (IoT)|[[Internet of Things Internet of Things (IoT)|[[Internet of Things Internet of Things (IoT)|[[Internet of Things (IoT)|[[Internet of Things (IoT)|[[Internet of Things (IoT)|[[Internet of Things (IoT)|[[ Internet of Things Internet of Things (IoT)|[[Internet of Things (IoT)|[[Internet of Things (IoT)|[[Internet of Things (IoT)|Internet of Things (IoT) ]]] ]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]. Companies' spending on cybersecurity for IoT systems reached $1.17 billion in 2017, up 29% from the previous year, when costs were measured at $912 million.
Most of the market under consideration was accounted for by professional services, which in 2017 were provided in the amount of $734 million against $570 million a year earlier. The gateway and user equipment security segments recorded investments of $138 million and $302 million, respectively. In 2016, these figures were measured at 240 and 102 million dollars.

The study notes that cyber attacks on the Internet of Things have become a reality. About 20% of organizations surveyed by Gartner faced them between 2015 and 2018.
According to Gartner analyst Ruggero Contu, when deploying the Internet of Things, companies often do not pay attention to the sources of purchase of equipment and software, as well as their features.
It is predicted that even before 2020, the security of the Internet of Things will not be a priority for businesses. In addition, the introduction of the best information security practices and tools in IoT planning will be ignored. Because of these two constraining factors the market of information security solutions for Internet of Things will lose 80% of potential revenue.
According to experts, the main growth driver of the market under consideration is the demand for tools and services that improve threat detection and asset management, equipment and software security assessment, as well as testing for the protection of IoT systems from unauthorized access. Thanks to these factors, spending on information security for the Internet of Things will grow to $3.1 billion in 2021, Gartner predicts.
Incident History
2020
Data of 515 thousand servers, home routers and IoT devices were in the public domain
The cybercriminal has released Telnet credentials for more than 515,000 servers, home routers, and IoT devices. This became known on January 20, 2020. Read more.
Sexual extortion through smart cameras
In mid-January 2020, researchers sounded the alarm due to a wave of a new type of fraud - sexual extortion amid panic over the security of smart cameras.
Concerns about internet-connected cameras, combined with a simple e-mail distribution, allow the unsuspecting victim to be deceived. A wave of a new version of an old scam has swept through the network - the criminals are trying to convince the victim that they have incriminating information that they will release to the public if they are not paid a ransom. Now the scammers claim to have obtained the sex tapes from smart security cameras and threaten to upload them to the public network or send them to the victim's friends.

Researchers from the Mimecast company have recorded a huge surge in a new type of fraud: in just two days from January 2 to 3, more than 1,600 fraudulent emails were intercepted. The attackers write that they have several incriminating photos or videos and provide a link to a website that displays the usual footage from security cameras in a common area, such as a bar or restaurant - a place that anyone could have visited in the past week. This footage is intended to convince the victim that his or her compromising actions were recorded using security cameras or a smartphone.
In fact, such a video does not exist, and scammers simply cast a bait, hoping that the victim will take the bait. This is a very cheap and incredibly effective scam. In 2018, the total number of email extortion complaints increased by 242%, and experts are warning users not to respond to threats and contact the police immediately.
2019
75% of attacks on IoT devices are in the US
According to Nikolai Murashov, since 2015, the trend of using DDoS attacks using Internet of Things botnets has been maintained. Such devices include, for example, home routers, webcams, smart home devices, wellness controls, etc. Such devices are often hacked, captured in a botnet and used to attack other objects, including CII objects, leads he is an example. Nikolay Murashov warns that the totality of such attacks using botnets can be so large that it can lead to disruption of the Internet network in the entire region.
FBI: Each IoT Device Needs a Separate Network
The bureau's cybersecurity experts recommend using two internet gateways: one for devices that store sensitive data and another for digital assistants such as home security devices, smart watches, game systems, fitness trackers, thermostats, smart light bulbs, etc. e. It is also recommended to change all factory default passwords.

According to the FBI, potential vulnerabilities in IoT devices allow hackers to gain access to the router's network, thereby providing access to other connected devices on the home network. Creating separate network systems will prevent intruders from invading the main devices.
In addition, experts recommend using microsegmentation. This function, available in the built-in software most WiFi routers: it allows router administrators to create virtual networks (VLANs) that behave like different networks, even if they are running on the same router.
In general, the FBI has proposed the following digital defense principles:
105 million attacks on IoT devices recorded in the first half of the year
On October 16, 2019, it became known that in the first half of 2019, specialists from Kaspersky Lab, using honeypots (a resource that is a bait for intruders), recorded 105 million attacks on IoT devices coming from 276 thousand unique addresses. This figure is seven times higher than in the first half of 2018, when about 12 million attacks were detected from 69,000 IP addresses. Taking advantage of the weak protection of IoT products, cybercriminals are putting more effort into creating and monetizing IoT botnets.
The number of cyberattacks on IoT devices is rapidly increasing as more and more users and organizations acquire "smart" devices, such as routers or video recording cameras, but not everyone cares about their protection. Cybercriminals, in turn, see more and more financial opportunities in the use of such devices. They use networks of infected smart devices to carry out DDoS attacks or as a proxy for other types of malicious activity.
Among the states from whose territory attacks on the honeypots of Kaspersky Lab originated, China was in the first place, Brazil was in the second; followed by Egypt and Russia with a gap of 0.1%. The observed trends generally continued throughout 2018 and 2019 with little change in the ranking of countries by the number of attacks.


Trend Micro finds out how cybercrime groups use IoT devices
On September 10, 2019 the Trend Micro company published the study "Uncovering IoT Threats in the Cybercrime Underground" which describes how cybercriminal groups use IoT devices for their own purposes and what threats it creates.
Trend Micro analysts researched the dark web, figuring out which IoT vulnerabilities are most popular among cybercriminals, as well as what languages are spoken by members of the cyber underground. During the study, it turned out that the Russian language was among the five most popular on the Darknet. In addition to Russian, the top 5 dark web languages include English, Portuguese, Spanish, and Arabic. The report provides an analysis of five cybercriminal communities classified according to the languages they use to communicate. Language proved to be a more important unifying factor than geographic location.

2017
Gemalto: Consumers have no confidence in the security of IoT devices
Gemalto published data in October 2017: it turns out that 90% of consumers do not trust the security of Internet of Things (Internet of Things or IoT) devices. That's why more than two-thirds of consumers and almost 80% of organizations have supported governments taking action to secure the IoT.
Consumers' top concerns (according to two-thirds of respondents) relate to hackers who could take control of their device. In fact, it's more of a concern than data breaches (60%) and hacker access to personal information (54%). Even though more than half (54%) of consumers own IoT devices (on average, two devices per person), only 14% consider themselves well aware of the security of these devices. These statistics show that both consumers and businesses need to additional education in this area.
In terms of the level of investment in security, the survey showed that IoT device manufacturers and service providers spend only 11% of their total IoT budget on securing IoT devices. The study found that these companies truly recognize the importance of protecting devices and the data they generate or transmit, with 50% of companies providing security based on project approach. Two-thirds (67%) of organizations report using encryption as their primary method of protecting IoT assets, with 62% data encryption as soon as it reaches the IoT device and 59% as it leaves the device. Ninety-two percent of companies saw an increase in sales or product usage after implementing IoT security measures.
Support for IoT security rules gains momentum
According to the survey, companies support provisions that make it clear who is responsible for securing IoT devices and data at every stage of their use (61%) and what the consequences of non-compliance with security are (55%). In fact, almost every organization (96%) and every consumer (90%) have a need for government-level IoT security regulations.
Lack of comprehensive opportunities to build partnerships
Fortunately, companies are gradually realizing that they need support in understanding IoT technology and are turning to partners for help, with the highest preference for cloud service providers (52%) and vendors. IoT services(fifty%). They most often cite lack of experience and skills as the main reason for this appeal (47%), followed by help and acceleration of the deployment of the Internet of Things (46%).
While such partnerships can benefit businesses as they implement the IoT, organizations recognize that they do not have full control over the data collected by IoT products or services as that data moves from partner to partner, potentially leaving it insecure. .







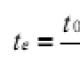


For beginners: breeding a broiler at home Boiled water for broilers
Only lovers will survive
Features of advertising aimed at children
retouching old photos in photoshop retouching old photos
What is an NPO: decoding, definition of goals, types of activities Does a non-profit organization have the right